Cybercriminal Makes Millions From Executive Office365 Account Hacks
Table of Contents
Methods Used by Cybercriminals to Hack Executive Office365 Accounts
Cybercriminals employ various methods to breach the security of executive Office365 accounts. These sophisticated attacks often combine multiple techniques to maximize their chances of success. Let's explore some of the most common approaches:
-
Phishing Attacks: These are perhaps the most prevalent method. Cybercriminals craft highly personalized emails designed to mimic legitimate communications from trusted sources. These spear phishing emails often include urgent requests, fake invoices, or notifications requiring immediate action, pressuring the recipient to click malicious links or download infected attachments. The personalization increases the likelihood of success, particularly with executives who often handle sensitive information and deal with time-sensitive matters.
-
Credential Stuffing: This technique involves using stolen usernames and passwords from other data breaches to attempt to access Office365 accounts. Cybercriminals leverage vast databases of compromised credentials, systematically trying different combinations until they find a match. This highlights the importance of using unique, strong passwords for every account.
-
Malware Attacks: Malicious software, such as Trojans and keyloggers, can be deployed through various means, including phishing emails or infected websites. Once installed, this malware can capture keystrokes, steal credentials, and grant the attacker remote access to the compromised system and the Office365 account.
-
Social Engineering: This involves manipulating individuals into divulging sensitive information or performing actions that compromise security. This could include pretexting (pretending to be someone else), baiting (offering something enticing in exchange for information), or quid pro quo (offering a service in exchange for sensitive data).
-
Multi-Factor Authentication (MFA) Bypass: While MFA is a crucial security layer, attackers are constantly seeking ways to bypass it. This might involve exploiting vulnerabilities in MFA systems or using social engineering techniques to trick users into revealing their authentication codes.
The High Value of Executive Office365 Accounts
Executive Office365 accounts represent highly valuable targets for cybercriminals due to the sensitive information they provide access to. This includes:
-
Sensitive Data: Executives often have access to confidential company data, including strategic plans, financial records, intellectual property, customer information, and merger and acquisition details. This data can be incredibly valuable to competitors or used for extortion.
-
Financial Information: Executive accounts may provide access to banking details, payment systems, and investment strategies, enabling cybercriminals to initiate fraudulent transactions or steal funds.
-
Corporate Secrets: Compromising an executive account can give attackers access to sensitive information about business dealings, potentially impacting negotiations and corporate decisions.
-
Insider Threats: A compromised executive account can be leveraged to facilitate insider threats, enabling attackers to manipulate internal systems and steal data undetected. This is due to the high level of trust and access associated with executive roles.
-
Privileged Access: Executive accounts often come with extensive privileges, granting access to various corporate systems and data sources. This privileged access significantly increases the potential damage from a successful attack.
Protecting Your Organization from Office365 Executive Account Hacks
Protecting your organization from Office365 executive account hacks requires a multi-layered approach incorporating best practices and advanced security tools. Here are some key steps:
-
Strong Passwords and Password Management: Enforce strong, unique passwords for all accounts and implement a robust password management policy. Consider using a password manager to help employees create and securely store complex passwords.
-
Multi-Factor Authentication (MFA): Implement and enforce MFA for all Office365 accounts, especially those at the executive level. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they obtain usernames and passwords.
-
Security Awareness Training: Regularly train employees, particularly executives, on cybersecurity best practices, including phishing awareness, social engineering tactics, and safe browsing habits. Simulate phishing attacks to test employee vigilance and reinforce training.
-
Data Loss Prevention (DLP): Utilize DLP tools to monitor and prevent sensitive data from leaving the organization's network. This includes email monitoring, data encryption, and access control measures.
-
Threat Detection and Response: Invest in robust threat detection and response systems to identify and mitigate attacks quickly. This involves continuous monitoring, intrusion detection, and incident response planning.
Conclusion:
The financial consequences of Office365 executive account hacks are substantial, as demonstrated by the success of cybercriminals who exploit these vulnerabilities for massive financial gain. The methods used are varied and sophisticated, highlighting the need for a proactive, multi-layered approach to cybersecurity. To prevent Office365 account breaches, organizations must prioritize strong passwords, enforce multi-factor authentication, invest in comprehensive employee training, and implement robust threat detection and response systems. Secure your executive Office365 accounts by taking these steps today. Visit our resource page for more information on strengthening your Office365 security and safeguarding your organization from this ever-evolving threat. Contact a cybersecurity specialist to assess your current security posture and develop a tailored security plan.

Featured Posts
-
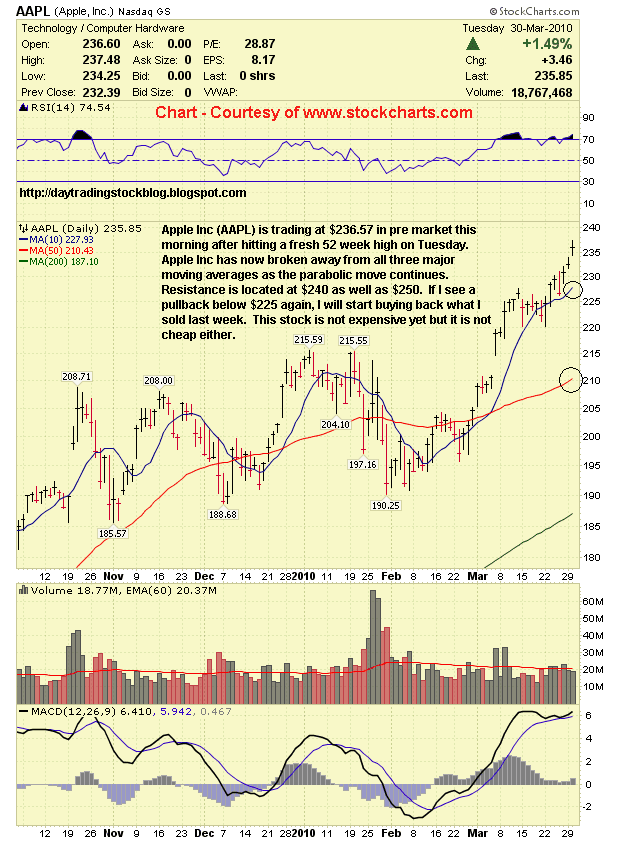 Aapl Stock Analysis Identifying Crucial Price Levels
May 25, 2025
Aapl Stock Analysis Identifying Crucial Price Levels
May 25, 2025 -
 Naomi Kempbell 55 Rokiv Stil Ikoni Podiumu
May 25, 2025
Naomi Kempbell 55 Rokiv Stil Ikoni Podiumu
May 25, 2025 -
 Luxury Carmakers Face Headwinds In The Chinese Market Case Studies Of Bmw And Porsche
May 25, 2025
Luxury Carmakers Face Headwinds In The Chinese Market Case Studies Of Bmw And Porsche
May 25, 2025 -
 Shareholders Approve All Resolutions At Imcd N V S Annual General Meeting
May 25, 2025
Shareholders Approve All Resolutions At Imcd N V S Annual General Meeting
May 25, 2025 -
 Stock Market Update Amsterdam Plunges 7 On Trade War Fears
May 25, 2025
Stock Market Update Amsterdam Plunges 7 On Trade War Fears
May 25, 2025
Latest Posts
-
 Is Naomi Campbell Banned From The 2025 Met Gala A Wintour Feud Explored
May 25, 2025
Is Naomi Campbell Banned From The 2025 Met Gala A Wintour Feud Explored
May 25, 2025 -
 Naomi Campbell And Anna Wintours Feud The Truth Behind The Met Gala Ban Rumors
May 25, 2025
Naomi Campbell And Anna Wintours Feud The Truth Behind The Met Gala Ban Rumors
May 25, 2025 -
 Naomi Campbells Alleged Met Gala 2025 Ban Feud With Anna Wintour
May 25, 2025
Naomi Campbells Alleged Met Gala 2025 Ban Feud With Anna Wintour
May 25, 2025 -
 Naomi Kempbell Svyatkuye Yuviley Divitsya Novi Foto
May 25, 2025
Naomi Kempbell Svyatkuye Yuviley Divitsya Novi Foto
May 25, 2025 -
 Deti Naomi Kempbell Podrosli Foto I Podrobnosti O Lichnoy Zhizni Supermodeli
May 25, 2025
Deti Naomi Kempbell Podrosli Foto I Podrobnosti O Lichnoy Zhizni Supermodeli
May 25, 2025
