Cybercriminal's Office365 Scheme: Millions In Profit From Executive Inboxes

Table of Contents
Understanding the Office365 Executive Email Compromise (EEC) Threat
Executive Email Compromise (EEC), also known as Business Email Compromise (BEC), is a sophisticated form of phishing attack that specifically targets high-level employees within an organization. The impact on businesses can be devastating. These attacks are highly successful because they leverage trust and authority.
- High success rate due to targeting high-level employees: Executives often have access to sensitive financial information and authority to make significant financial decisions, making them prime targets.
- Significant financial losses from fraudulent wire transfers: The primary goal is often to initiate fraudulent wire transfers, resulting in substantial financial losses for the victimized company. Millions of dollars can be lost in a single attack.
- Reputational damage and loss of customer trust: A successful EEC attack can severely damage a company's reputation, leading to a loss of customer trust and potential business partnerships.
- Legal repercussions and regulatory fines: Organizations may face legal repercussions and hefty regulatory fines for failing to implement adequate security measures to protect sensitive data.
Cybercriminals employ various methods to gain access to executive inboxes:
- Spear-phishing emails mimicking trusted sources: These emails are carefully crafted to appear legitimate, often impersonating clients, vendors, or even colleagues.
- Exploiting vulnerabilities in third-party apps connected to Office365: Compromising third-party apps integrated with Office365 can provide an entry point for attackers.
- Using stolen credentials obtained through various methods: Stolen credentials, often obtained through password dumps or credential stuffing attacks, grant direct access to accounts.
- Leveraging social engineering techniques: Manipulating individuals through psychological tactics to gain access or information is a common tactic.
Common Tactics Used in Office365 BEC Scams
BEC scams targeting Office365 users are highly manipulative and often rely on urgency and deception.
- Urgency and pressure tactics in email requests: Attackers create a sense of urgency, pressuring executives to act quickly without proper verification.
- Impersonating known contacts or executives: Emails may appear to be from a trusted colleague, superior, or client, increasing the likelihood of a response.
- Manipulating payment details and instructions: Attackers subtly alter payment instructions, diverting funds to their own accounts.
- Requesting wire transfers to unfamiliar accounts: These transfers often go to accounts controlled by the attackers, hidden behind layers of obfuscation.
Compromised accounts can also be used for internal communication, furthering the deception:
- Sending emails appearing to come from trusted colleagues: Attackers can use compromised accounts to send internal emails requesting sensitive information or authorization for fraudulent transactions.
- Requesting sensitive information internally: Internal emails may ask for financial data, passwords, or other sensitive information under the guise of legitimate requests.
- Accessing financial data and internal systems: Once access is gained, attackers can exploit this to access financial data and potentially other internal systems.
Protecting Your Business from Office365-Based Cyberattacks
Protecting your business from Office365-based cyberattacks requires a multi-layered approach focusing on both technical safeguards and employee education.
The importance of multi-factor authentication (MFA) cannot be overstated:
- Implementing strong passwords and password management tools: Use strong, unique passwords for all accounts and leverage password managers to streamline the process.
- Regularly updating software and patches: Keeping all software and applications up-to-date patches vulnerabilities that attackers could exploit.
- Enforcing strict email security policies: Establish clear policies regarding email usage, including handling of sensitive information and suspicious emails.
- Training employees on identifying phishing emails: Regular training is crucial for empowering employees to recognize and report suspicious emails.
Advanced security features are essential:
- Utilizing advanced threat protection and anti-malware solutions: Implementing advanced security solutions can detect and block malicious emails and attachments.
- Regularly reviewing user access permissions: Regularly review and revoke unnecessary access permissions to minimize the impact of a potential compromise.
- Implementing robust data loss prevention (DLP) measures: DLP helps prevent sensitive data from leaving the organization's network.
- Conducting regular security audits and penetration testing: Regular security assessments identify vulnerabilities and weaknesses before attackers can exploit them.
Security awareness training is paramount:
- Phishing simulations to identify vulnerabilities: Regular phishing simulations help identify weak points in your employees' security awareness.
- Regular training on best practices to avoid scams: Consistent training reinforces best practices and helps employees stay vigilant against social engineering tactics.
- Promoting a security-conscious culture: Cultivate a security-conscious culture where employees feel empowered to report suspicious activity.
Conclusion
Office365-based cybercriminal schemes targeting executive inboxes represent a significant threat, capable of causing substantial financial and reputational damage. The sophisticated tactics employed highlight the need for proactive security measures. Multi-factor authentication (MFA), robust employee training, and advanced security features like email authentication protocols (SPF, DKIM, DMARC) are crucial for mitigating this risk. Don't become another victim of Office365 executive email compromise. Implement robust security measures today to protect your business from these costly attacks. Learn more about strengthening your Office365 security now and safeguard your valuable data and reputation.

Featured Posts
-
 Inter Milan Stuns Barcelona Reaches Champions League Final
May 08, 2025
Inter Milan Stuns Barcelona Reaches Champions League Final
May 08, 2025 -
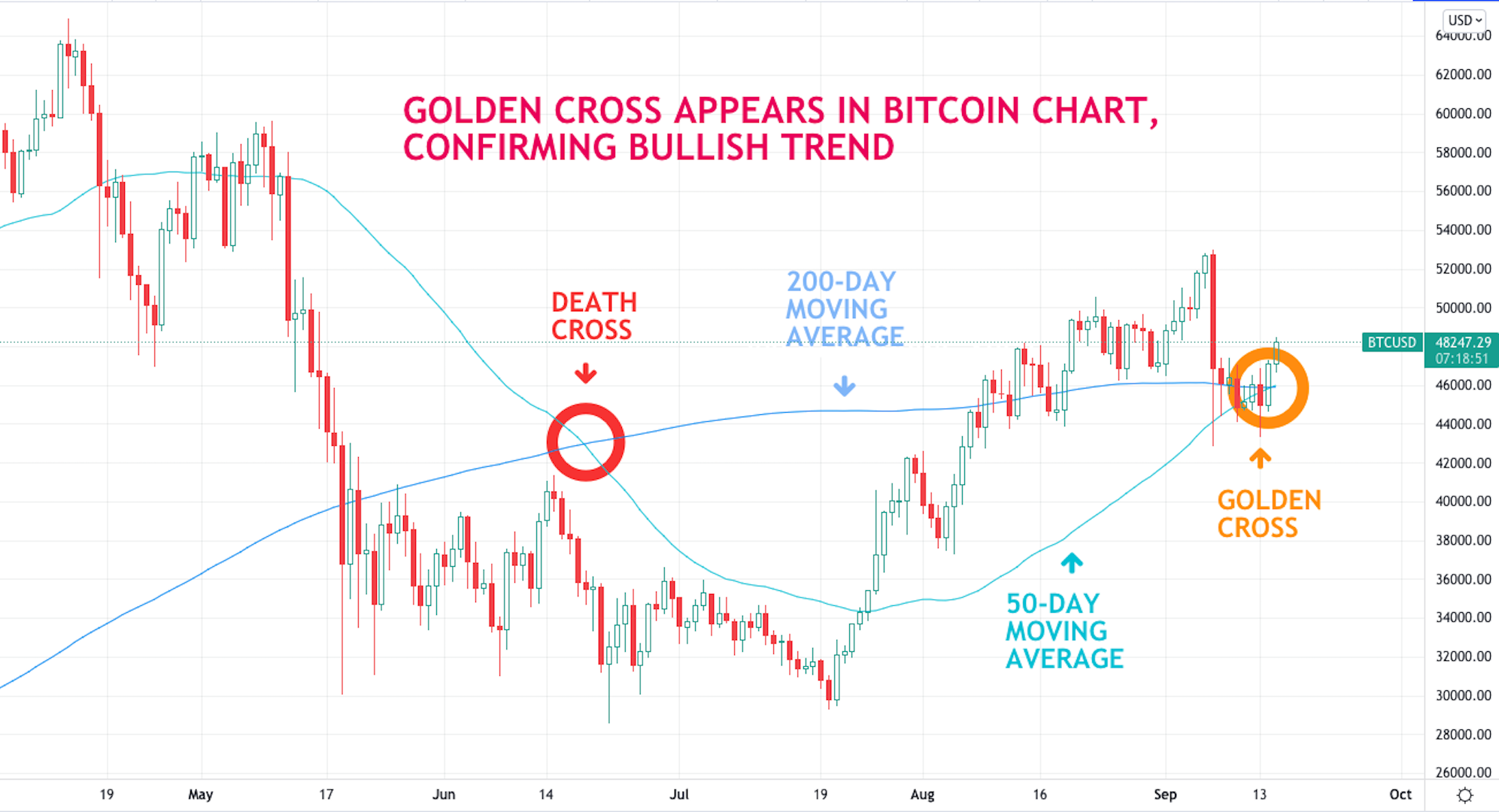 Bitcoin Golden Cross Implications For Price And Market
May 08, 2025
Bitcoin Golden Cross Implications For Price And Market
May 08, 2025 -
 Papa Francisco Fieis Passam A Noite Nas Ruas Do Vaticano
May 08, 2025
Papa Francisco Fieis Passam A Noite Nas Ruas Do Vaticano
May 08, 2025 -
 Ps 5 Vs Xbox Series S Which Console Should You Choose
May 08, 2025
Ps 5 Vs Xbox Series S Which Console Should You Choose
May 08, 2025 -
 Washingtons Openness To Canadas Trade Proposals
May 08, 2025
Washingtons Openness To Canadas Trade Proposals
May 08, 2025
Latest Posts
-
 Browns Bolster Receiving Corps With Veteran Signing
May 08, 2025
Browns Bolster Receiving Corps With Veteran Signing
May 08, 2025 -
 Nuggets Westbrook Leads Jokics Birthday Celebration With Special Rendition
May 08, 2025
Nuggets Westbrook Leads Jokics Birthday Celebration With Special Rendition
May 08, 2025 -
 De Andre Jordan Otkriva Prava Prica Iza Poljubaca Sa Jokicem
May 08, 2025
De Andre Jordan Otkriva Prava Prica Iza Poljubaca Sa Jokicem
May 08, 2025 -
 Veteran Wide Receiver Joins Cleveland Browns Roster
May 08, 2025
Veteran Wide Receiver Joins Cleveland Browns Roster
May 08, 2025 -
 Zasto Se De Andre Jordan I Nikola Jokic Ljube Tri Puta Objasnjenje
May 08, 2025
Zasto Se De Andre Jordan I Nikola Jokic Ljube Tri Puta Objasnjenje
May 08, 2025
