Cybercriminal's Office365 Scheme: Millions Stolen From Executive Accounts
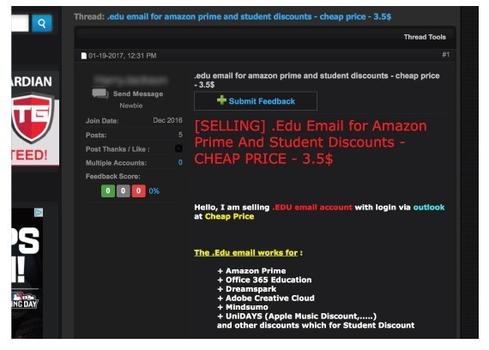
Table of Contents
Understanding the Office 365 Attack Vector
Cybercriminals employ various methods to gain unauthorized access to Office 365 accounts. Once inside, they can access a wealth of sensitive information, including emails, documents, financial records, and strategic plans. Access to executive accounts is particularly damaging, allowing attackers to initiate large-scale financial fraud and inflict significant reputational harm.
Here are some common attack methods:
- Phishing Emails: These emails often mimic legitimate communications, using convincing subject lines like "Urgent Invoice," "Important Security Update," or personalized greetings. They may contain malicious links or attachments that download malware onto the victim's device, granting access to their credentials.
- Credential Stuffing and Brute-Force Attacks: Attackers use lists of stolen usernames and passwords (credential stuffing) or automated tools (brute-force attacks) to try and guess login details. Weak passwords make these attacks significantly more successful.
- Exploiting Third-Party App Vulnerabilities: Many businesses integrate third-party apps with Office 365. If these apps have security flaws, attackers can exploit them to gain access to the platform.
- Compromised Employee Devices: Infected laptops or mobile devices can provide a backdoor into Office 365 if employees use the same credentials on multiple platforms.
Once an account is compromised, attackers can easily access and exfiltrate sensitive company data. This access to executive accounts, in particular, allows for larger-scale financial theft through fraudulent wire transfers and manipulation of financial systems.
Common Tactics Used in Office 365 Scams
After gaining access, cybercriminals utilize various schemes to maximize their gains. These attacks are often highly sophisticated and difficult to detect in their early stages.
- Business Email Compromise (BEC): Attackers impersonate executives to send emails requesting urgent wire transfers or other financial transactions. The seemingly legitimate communication can easily deceive employees.
- Data Exfiltration: Sensitive data, such as customer information, intellectual property, financial records, and strategic plans, is stolen and may be used for further malicious activities like ransomware attacks, blackmail, or identity theft.
- Account Takeover for Malicious Purposes: Compromised accounts can be used to send spam emails, deploy malware to other employees, or participate in wider phishing campaigns.
Numerous real-world examples highlight the devastating consequences of these attacks. Reports from sources like the FBI's Internet Crime Complaint Center (IC3) frequently detail significant financial losses resulting from Office 365 compromises. The sophistication of these attacks necessitates a proactive and multi-layered approach to security.
Protecting Your Business from Office 365 Attacks
Protecting your business from these sophisticated attacks requires a multi-pronged strategy focusing on prevention, detection, and response.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring more than just a password to access accounts. It's crucial for minimizing the risk of unauthorized access.
- Strong Password Policies: Enforce strong, unique passwords and implement regular password changes. Consider password managers to assist employees.
- Security Awareness Training: Educate employees to identify and avoid phishing attempts. Regular training simulations are effective.
- Regular Software Updates: Keep all software and operating systems updated to patch known vulnerabilities.
- Robust Email Security Solutions: Implement email security solutions with advanced anti-phishing and anti-malware filters.
- Advanced Threat Protection: Utilize the advanced threat protection features offered by Office 365 itself.
- Regular Security Audits and Penetration Testing: Regularly assess your security posture to identify and address weaknesses.
- Incident Response Planning: Develop a comprehensive incident response plan to handle breaches effectively and minimize damage.
Engaging reputable cybersecurity firms for ongoing protection and support is highly recommended. They offer expertise in threat detection, vulnerability management, and incident response.
Safeguarding Your Business from Cybercriminal's Office365 Schemes
Office 365 compromises represent a significant threat to businesses, potentially leading to substantial financial losses and reputational damage. Proactive security measures are critical to prevent these attacks. By implementing multi-factor authentication, robust email security, employee training, and regular security audits, businesses can significantly reduce their vulnerability. Assess your current Office 365 security posture today. If you need assistance, seek professional help from a reputable cybersecurity firm to protect your business from similar Office 365 schemes. For further resources on enhancing your security, explore the cybersecurity best practices guides available online from reputable sources like the National Institute of Standards and Technology (NIST).

Featured Posts
-
 Beyonce Blue Ivy Carter And Kendrick Lamar Triumph At Naacp Image Awards
Apr 30, 2025
Beyonce Blue Ivy Carter And Kendrick Lamar Triumph At Naacp Image Awards
Apr 30, 2025 -
 Bet Mgm Rotobg 150 150 Bonus For Tonights Warriors Rockets Game
Apr 30, 2025
Bet Mgm Rotobg 150 150 Bonus For Tonights Warriors Rockets Game
Apr 30, 2025 -
 Ev Mandate Faces Stiff Opposition From Car Dealers
Apr 30, 2025
Ev Mandate Faces Stiff Opposition From Car Dealers
Apr 30, 2025 -
 Fdyht Shbab Bn Jryr Ryys Alnady Yudan Qdayya
Apr 30, 2025
Fdyht Shbab Bn Jryr Ryys Alnady Yudan Qdayya
Apr 30, 2025 -
 Amanda Owen Opens Up About Life After Divorce And Future Goals
Apr 30, 2025
Amanda Owen Opens Up About Life After Divorce And Future Goals
Apr 30, 2025
Latest Posts
-
 Dagskra Bestu Deildarinnar Hvad Er I Bodi I Dag
Apr 30, 2025
Dagskra Bestu Deildarinnar Hvad Er I Bodi I Dag
Apr 30, 2025 -
 Tpbl
Apr 30, 2025
Tpbl
Apr 30, 2025 -
 Valur Vs Andstaedingur Horfdu A Leikinn I Dag
Apr 30, 2025
Valur Vs Andstaedingur Horfdu A Leikinn I Dag
Apr 30, 2025 -
 Edward Propels Minnesota Past Brooklyn With Dominant Performance
Apr 30, 2025
Edward Propels Minnesota Past Brooklyn With Dominant Performance
Apr 30, 2025 -
 Tpbl Mvp
Apr 30, 2025
Tpbl Mvp
Apr 30, 2025
