Executive Email Compromise: Millions Lost Through Office365 Account Breaches
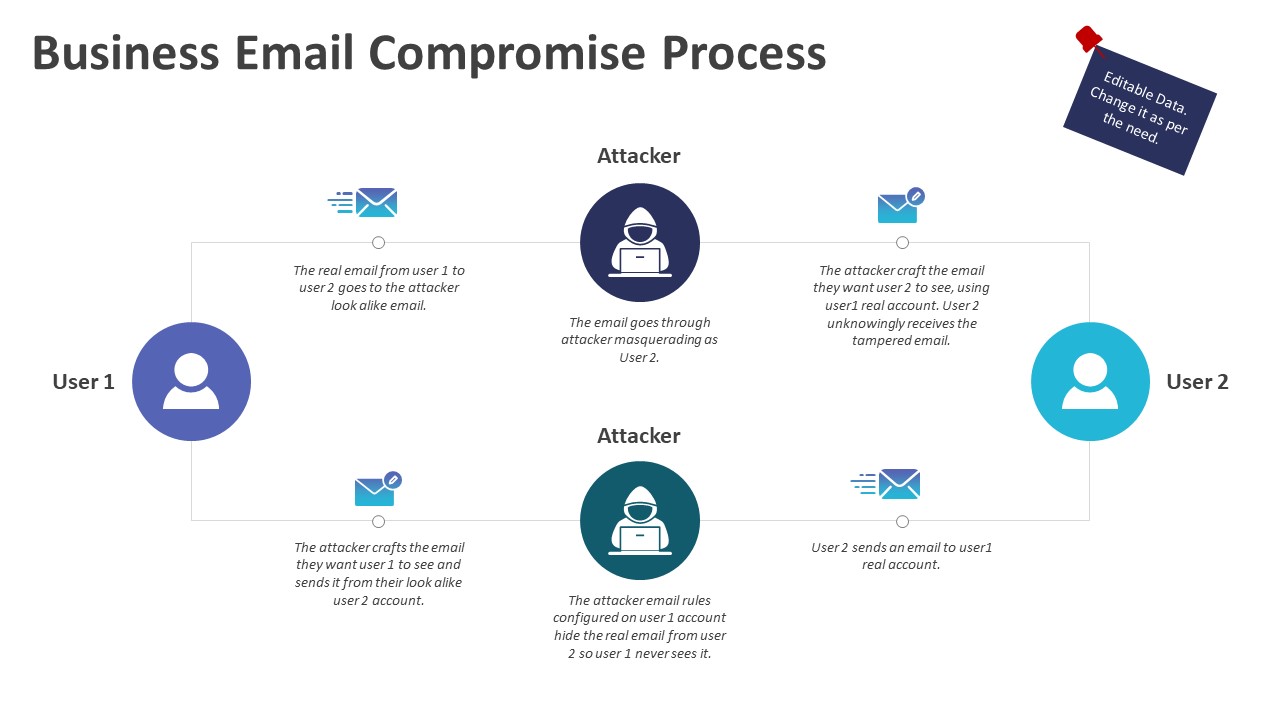
Table of Contents
Understanding the Mechanisms of Executive Email Compromise (EEC)
Phishing and Spear Phishing Attacks
Sophisticated phishing and spear-phishing emails are the primary vectors for EEC attacks. Attackers craft convincing emails that mimic legitimate communications from trusted sources, such as banks, legal firms, or even colleagues. These emails often create a sense of urgency, tricking executives into clicking malicious links or opening infected attachments.
- Examples of phishing techniques: Impersonating known individuals, using urgent subject lines, leveraging brand logos and official-looking email addresses.
- Social engineering tactics: Building rapport, exploiting trust, manipulating emotions to gain access to sensitive information.
- Urgency tactics: Creating a sense of immediate action required, preventing victims from carefully considering the email's authenticity.
- Attackers meticulously research their targets, gathering information to personalize emails and increase their effectiveness. They leverage social media, company websites, and other publicly available sources to craft highly targeted spear-phishing campaigns.
Malware and Credential Theft
Malware plays a crucial role in many EEC attacks. Keyloggers record keystrokes, capturing login credentials, while Trojans can provide attackers with remote access to the victim's computer and Office365 account.
- Types of malware used: Keyloggers, Trojans, ransomware, spyware.
- Methods of infection: Malicious links in emails, infected attachments, drive-by downloads.
- Once access is gained, attackers can access emails, initiate fraudulent wire transfers, manipulate invoices, and steal confidential data. They may also install further malware to maintain persistent access to the compromised system.
Exploiting Weak Passwords and Security Gaps
Weak passwords and insufficient security measures significantly increase the vulnerability of Office365 accounts to EEC attacks.
- Importance of strong, unique passwords: Using complex passwords that are difficult to guess or crack. Utilizing password managers to generate and store strong, unique passwords for each account.
- Multi-factor authentication (MFA): Implementing MFA adds an extra layer of security, requiring multiple forms of authentication to access an account, even if the password is compromised.
- Regular password changes: Enforcing regular password changes and encouraging employees to update their passwords frequently.
- Attackers often exploit easily guessed passwords, default credentials, or accounts with reused passwords across multiple platforms. They may also leverage known security vulnerabilities in Office365 or related applications to gain unauthorized access.
The High Cost of Office365 Account Breaches Due to EEC
Financial Losses
The financial consequences of EEC attacks can be devastating. Fraudulent wire transfers, invoice scams, and other BEC schemes result in significant financial losses for organizations.
- Examples of financial losses: Millions of dollars lost in fraudulent transactions, costly legal battles, and reputational damage.
- The scale of the problem is significant, with many companies suffering losses in the six- and seven-figure range. These financial losses can cripple small and medium-sized businesses and severely impact the bottom line of larger corporations.
Reputational Damage
EEC attacks not only cause financial losses but also inflict significant reputational damage. Loss of customer confidence, negative media coverage, and legal repercussions can have long-term consequences.
- Loss of customer confidence: Customers may lose trust in the organization’s ability to protect their data and financial information.
- Negative media coverage: Public disclosure of a data breach can result in negative publicity and damage to the company's brand image.
- Legal repercussions: Companies may face lawsuits from affected customers, partners, and regulatory bodies.
Regulatory Fines and Legal Consequences
Non-compliance with data protection regulations like GDPR and CCPA can lead to substantial fines and legal battles after an EEC attack.
- Examples of regulatory fines: Significant financial penalties imposed on organizations for failing to adequately protect customer data.
- Legal liabilities can include compensation for data breaches, legal fees, and potential criminal charges.
Protecting Your Organization from Executive Email Compromise
Implementing Robust Security Measures
Strengthening Office365 security is crucial in preventing EEC attacks.
- MFA: Mandatory multi-factor authentication for all users, especially executives.
- Strong password policies: Enforcing strong, unique passwords and regular password changes.
- Security awareness training: Educating employees on phishing tactics, social engineering, and secure email practices.
- Email authentication (SPF, DKIM, DMARC): Implementing these protocols helps verify the authenticity of emails and prevents spoofing.
Advanced Threat Protection
Advanced threat protection solutions play a vital role in detecting and blocking malicious emails and malware.
- Features of advanced threat protection software: Real-time threat detection, sandboxing, URL analysis, and anti-phishing capabilities.
- Benefits of using such solutions: Proactive threat detection, reduced risk of infection, improved security posture.
Employee Training and Awareness
Employee education is paramount in preventing EEC attacks.
- Importance of phishing awareness training: Regular training sessions to educate employees on recognizing and reporting suspicious emails.
- Identifying suspicious emails: Training employees to identify red flags, such as unexpected requests, grammatical errors, and urgent tones.
- Secure email practices: Educating employees about safe email habits, such as not clicking on unknown links or opening suspicious attachments.
Conclusion
Executive Email Compromise targeting Office365 accounts represents a serious and growing threat to businesses of all sizes. The financial losses, reputational damage, and legal consequences associated with EEC attacks are substantial. To protect your organization, implementing robust security measures, investing in advanced threat protection, and prioritizing employee training are critical. Secure your Office365 accounts now by adopting a multi-layered approach to email security, including strong password policies, multi-factor authentication, and comprehensive security awareness training. Prevent Executive Email Compromise today and learn more about protecting against email compromise. By prioritizing Office365 security and implementing email security best practices, you can significantly reduce your risk of falling victim to BEC attacks.

Featured Posts
-
 10 Year Old Girl Dies On Rugby Pitch A Communitys Grief
May 02, 2025
10 Year Old Girl Dies On Rugby Pitch A Communitys Grief
May 02, 2025 -
 Political Row Explodes Farage And Lowe Trade Accusations
May 02, 2025
Political Row Explodes Farage And Lowe Trade Accusations
May 02, 2025 -
 Avrupa Is Birligimizi Gelistirme Yolunda Kritik Adimlar
May 02, 2025
Avrupa Is Birligimizi Gelistirme Yolunda Kritik Adimlar
May 02, 2025 -
 Fortnite Item Shop The Return Of Beloved Skins After 1000 Days
May 02, 2025
Fortnite Item Shop The Return Of Beloved Skins After 1000 Days
May 02, 2025 -
 Sakiewicz O Solidarnosci I Republice Analiza Wypowiedzi I Ich Wyroznienia
May 02, 2025
Sakiewicz O Solidarnosci I Republice Analiza Wypowiedzi I Ich Wyroznienia
May 02, 2025
