Federal Charges Filed In Multi-Million Dollar Office365 Hacking Scheme
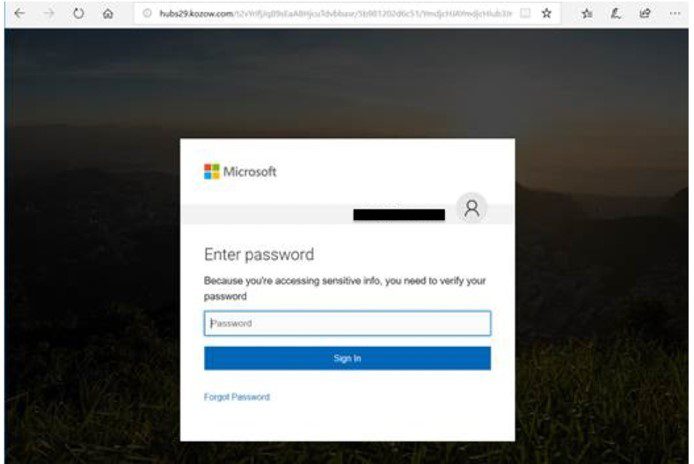
Table of Contents
Details of the Office365 Hacking Scheme
This large-scale Office365 hacking operation resulted in significant financial losses and a substantial data breach. Understanding the methods employed is crucial to preventing future incidents.
The Modus Operandi
The hackers allegedly employed a multi-pronged approach to breach Office365 accounts, leveraging several common techniques.
- Spear Phishing: Highly targeted phishing emails were sent to specific employees within targeted organizations, often mimicking legitimate communications from trusted sources. These emails contained malicious links or attachments designed to deliver malware.
- Credential Stuffing: The hackers used lists of stolen usernames and passwords obtained from other data breaches to attempt to access Office365 accounts. This technique exploits the reuse of passwords across multiple platforms.
- Exploiting Vulnerabilities: The hackers may have also exploited known vulnerabilities in Office365 or its related applications. This could involve zero-day exploits—newly discovered vulnerabilities unknown to Microsoft—or unpatched software flaws.
The stolen data included a range of sensitive information, impacting both organizations and individuals. This included:
- Financial records and banking details
- Intellectual property and proprietary business information
- Customer data, including personal identifiable information (PII)
Scale of the Operation
The Office365 security breach resulted in an estimated loss exceeding $[Insert Estimated Financial Loss Here] million. The scheme impacted [Insert Number] victims, including both large corporations and smaller businesses across [Insert Geographic Reach, e.g., North America, multiple countries]. The targets included a variety of sectors, demonstrating the wide-reaching nature of this Office365 hacking campaign.
The Federal Charges Filed
The Department of Justice has filed charges against several individuals and potentially organizations involved in this sophisticated Office365 hacking scheme.
Accused Individuals and Organizations
[Insert Names of Accused Individuals/Organizations if Publicly Available]. The individuals are facing a range of serious charges including:
- Wire fraud
- Conspiracy to commit wire fraud
- Identity theft
- Computer fraud and abuse
Potential Penalties
If convicted, the accused face significant penalties, including:
- Extensive jail sentences (potentially decades)
- Substantial financial fines
- Restitution to victims
Implications and Prevention Strategies for Office365 Security
This multi-million dollar Office365 hacking scheme underscores the critical need for proactive security measures. Reacting to a breach is far more costly and damaging than preventing one.
Best Practices for Preventing Office365 Breaches
To mitigate the risk of an Office365 security breach, organizations should implement the following security measures:
- Multi-Factor Authentication (MFA): Require MFA for all Office365 accounts. This adds an extra layer of security beyond just a password.
- Strong Passwords and Password Management: Enforce strong, unique passwords for all accounts and encourage employees to utilize password managers.
- Regular Security Updates: Keep all software, including Office365 and related applications, updated with the latest security patches.
- Employee Training on Phishing Awareness: Regularly train employees on identifying and reporting phishing emails and other social engineering attempts.
- Robust Security Protocols: Implement strict access control policies and regularly review user permissions within Office365.
The Importance of Proactive Security Measures
Proactive security is paramount. Instead of solely reacting to breaches, organizations must invest in:
- Regular Security Audits: Conduct regular audits of Office365 configurations to identify vulnerabilities.
- Penetration Testing: Simulate attacks to identify weaknesses in your security posture.
- Incident Response Planning: Develop a comprehensive plan to respond to and mitigate the impact of a security breach.
Conclusion
The multi-million dollar Office365 hacking scheme highlights the devastating consequences of inadequate security measures. The scale of this operation and the severity of the charges filed underscore the critical need for robust Office365 security practices. Strengthen your Office365 security today by implementing the best practices outlined above. Protect your business from costly Office365 hacking and avoid becoming the next victim. Learn more about preventing Office365 data breaches by [Insert Link to Relevant Resource on Office365 Security].

Featured Posts
-
 Assessing The Impact Of Trumps Tariffs On Us Manufacturing
May 06, 2025
Assessing The Impact Of Trumps Tariffs On Us Manufacturing
May 06, 2025 -
 Mindy Kalings Transformation Slim Figure Stuns Fans
May 06, 2025
Mindy Kalings Transformation Slim Figure Stuns Fans
May 06, 2025 -
 Australian Election Result Impact On Asset Prices
May 06, 2025
Australian Election Result Impact On Asset Prices
May 06, 2025 -
 Mindy Kalings Weight Loss A New Look At The Premiere
May 06, 2025
Mindy Kalings Weight Loss A New Look At The Premiere
May 06, 2025 -
 Trumps Trade Policy A Gamble On Economic Stability
May 06, 2025
Trumps Trade Policy A Gamble On Economic Stability
May 06, 2025
Latest Posts
-
 Warner Bros Discovery 1 1 Billion Advertising Revenue Loss Predicted Without Nba
May 06, 2025
Warner Bros Discovery 1 1 Billion Advertising Revenue Loss Predicted Without Nba
May 06, 2025 -
 Impact Of Lost Nba Rights Warner Bros Discovery Projects 1 1 Billion Ad Revenue Decline
May 06, 2025
Impact Of Lost Nba Rights Warner Bros Discovery Projects 1 1 Billion Ad Revenue Decline
May 06, 2025 -
 1 1 Billion At Stake How Warner Bros Discoverys Nba Absence Impacts Advertising
May 06, 2025
1 1 Billion At Stake How Warner Bros Discoverys Nba Absence Impacts Advertising
May 06, 2025 -
 Warner Bros Discoverys Nba Deal Loss A 1 1 Billion Advertising Revenue Hit
May 06, 2025
Warner Bros Discoverys Nba Deal Loss A 1 1 Billion Advertising Revenue Hit
May 06, 2025 -
 How To Stream All March Madness Games Online
May 06, 2025
How To Stream All March Madness Games Online
May 06, 2025
