Federal Charges Filed: Millions Lost In Office365 Executive Data Breach
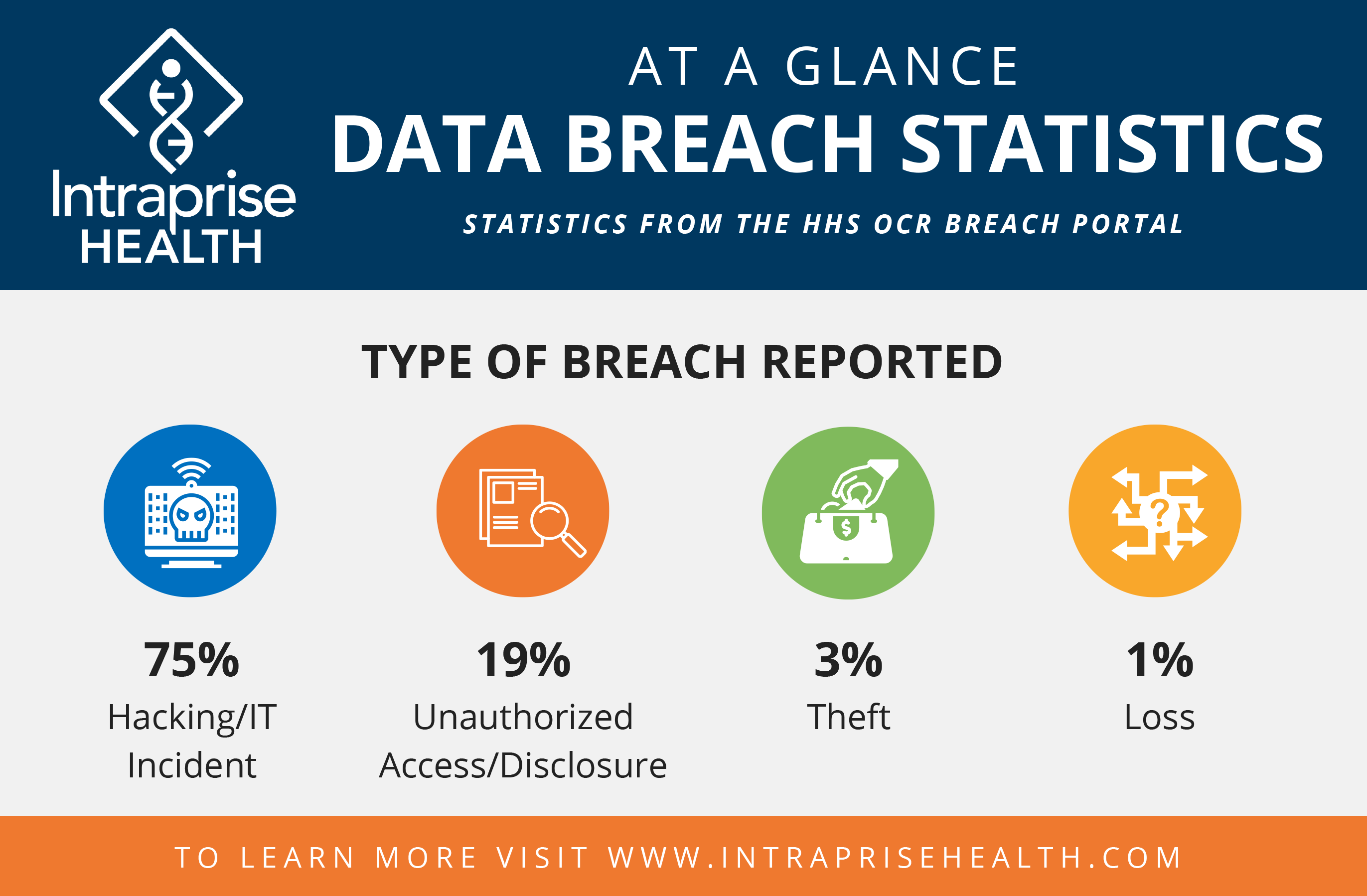
Table of Contents
The Scope of the Office365 Data Breach
The recent Office365 data breach represents a significant cybersecurity incident with far-reaching consequences. The financial losses alone amount to millions of dollars, impacting the bottom line of affected companies. This executive data breach extended beyond monetary damage, however. Critically, sensitive executive data, including confidential strategic plans, detailed financial records, and personal information of high-level executives, was compromised.
- Millions of dollars in financial losses reported. The exact figure may vary depending on ongoing investigations and legal proceedings, but the financial impact is substantial and demonstrates the high cost of inadequate cybersecurity.
- Sensitive executive data, including strategic plans, financial records, and personal information, compromised. This exposes the companies involved to significant risks, including intellectual property theft, reputational damage, and potential legal repercussions.
- The number of affected executives and companies involved remains undisclosed at this time. This is due to ongoing investigations and the sensitive nature of the information. However, reports suggest a significant number of executives across multiple organizations were affected.
- Types of data stolen included intellectual property, customer data, and financial statements. This wide range of compromised data underscores the breadth of the attack and the potential for long-term consequences.
- Impact on company reputation and shareholder confidence is substantial. News of the breach can lead to decreased investor trust, affecting stock prices and overall market valuation. The long-term reputational damage can be difficult to overcome.
Federal Charges Filed: Details of the Investigation
Following the discovery of the breach, a thorough cybercrime investigation was launched by federal law enforcement agencies. This resulted in the filing of federal charges against the individuals suspected of perpetrating the attack. The specifics of the charges are still emerging, but they are expected to include serious offenses related to data theft, unauthorized access, and potentially other violations of federal cybercrime statutes.
- Specific charges filed against the individuals or organizations involved are still under seal in some cases. However, anticipated charges include counts of wire fraud, computer fraud and abuse, and potentially conspiracy.
- Details about the investigation, including the agencies involved and the duration of the investigation, are still being released gradually. The complexity of the case requires careful analysis and evidence gathering.
- Evidence used to build the case included IP addresses, malware analysis, and digital forensic examinations. These investigations allow authorities to trace the activities of the perpetrators and build a strong case for prosecution.
- Potential penalties and sentencing guidelines vary significantly depending on the specific charges and the individuals' prior records. Severe penalties, including lengthy prison sentences and substantial fines, are anticipated.
- The legal implications for the compromised companies are considerable. They may face lawsuits from affected executives, customers, or shareholders. Regulatory fines and reputational damage are also significant concerns.
Analyzing the Vulnerabilities: How the Breach Occurred
The investigation is still ongoing, but initial reports suggest that the breach was likely facilitated by a combination of sophisticated techniques and inadequate security practices. The perpetrators may have exploited known vulnerabilities in Office365 or employed social engineering tactics, such as highly targeted phishing emails.
- Likely method of breach: a sophisticated phishing campaign targeting executive-level employees. This highlights the importance of security awareness training for all employees, not just IT staff.
- Inadequate security practices: lack of multi-factor authentication (MFA) was a significant contributing factor. The absence of MFA makes it easier for attackers to gain access even if they obtain login credentials.
- Weak passwords and a lack of robust password management policies were also identified as contributing factors. Strong, unique passwords for each account are crucial for enhanced security.
- Specific Office365 features targeted are still under investigation. However, the attackers may have exploited vulnerabilities in specific Office365 applications or services.
- The importance of regular security audits and penetration testing cannot be overstated. These proactive measures help identify vulnerabilities before malicious actors can exploit them.
Best Practices for Preventing Office365 Data Breaches
The Office365 data breach underscores the critical need for proactive and comprehensive cybersecurity measures. Organizations must prioritize robust security practices to protect their sensitive data and prevent future breaches.
- Implementing multi-factor authentication (MFA) for all user accounts is paramount. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Enforcing strong password policies and promoting password management best practices is essential. Regular password changes and the use of password managers can significantly enhance security.
- Providing regular cybersecurity awareness training for employees is crucial. Training should cover phishing scams, social engineering tactics, and password security best practices.
- Regularly patching and updating Office365 and related software is critical. Keeping software up-to-date patches security vulnerabilities and minimizes the risk of exploitation.
- Utilizing advanced threat protection features within Office365 offers added security layers. These features can help detect and prevent malicious activity.
- Implementing data loss prevention (DLP) tools helps protect sensitive information from unauthorized access or exfiltration. DLP tools monitor data movement and can prevent sensitive data from leaving the organization's network.
- Conducting regular security audits and penetration testing identifies vulnerabilities and weaknesses in the system. These assessments help organizations proactively address security gaps.
- Developing and regularly updating a comprehensive incident response plan is essential. A well-defined plan ensures a coordinated and effective response in the event of a security incident.
Conclusion
The Office365 executive data breach serves as a stark reminder of the ever-present threat of cybercrime. The millions of dollars lost and the federal charges filed demonstrate the severe consequences of inadequate cybersecurity measures. By implementing robust security practices, including strong password policies, multi-factor authentication, and regular employee training, organizations can significantly reduce their vulnerability to similar attacks. Don't wait for an Office365 data breach to strike – take proactive steps to protect your sensitive data today. Invest in comprehensive Office365 security solutions and ensure your organization is prepared to withstand the ever-evolving landscape of cyber threats. Strengthen your Office365 security now and mitigate the risk of becoming the next victim of a devastating data breach.

Featured Posts
-
 Khai Mac Giai Bong Da Thanh Nien Thanh Pho Hue Lan Thu Vii Thong Tin Chi Tiet Va Lich Thi Dau
May 01, 2025
Khai Mac Giai Bong Da Thanh Nien Thanh Pho Hue Lan Thu Vii Thong Tin Chi Tiet Va Lich Thi Dau
May 01, 2025 -
 Kashmiri Cat Owners Alarmed By Viral Social Media Posts
May 01, 2025
Kashmiri Cat Owners Alarmed By Viral Social Media Posts
May 01, 2025 -
 Fotboltadagskra Leikir I Bestu Deild Karla
May 01, 2025
Fotboltadagskra Leikir I Bestu Deild Karla
May 01, 2025 -
 Ramos Leads France To Six Nations Victory Scotland Rout
May 01, 2025
Ramos Leads France To Six Nations Victory Scotland Rout
May 01, 2025 -
 Six Nations 2025 Frances Path To Continued Excellence
May 01, 2025
Six Nations 2025 Frances Path To Continued Excellence
May 01, 2025
Latest Posts
-
 Outdated Apps The Hidden Cost In Your Ai Transformation
May 01, 2025
Outdated Apps The Hidden Cost In Your Ai Transformation
May 01, 2025 -
 Spd Waehlt Lars Klingbeil Zum Fraktionschef
May 01, 2025
Spd Waehlt Lars Klingbeil Zum Fraktionschef
May 01, 2025 -
 The Spds Role In Germanys New Government A Comprehensive Overview
May 01, 2025
The Spds Role In Germanys New Government A Comprehensive Overview
May 01, 2025 -
 Bayern President Rejects Far Right Af D Involvement
May 01, 2025
Bayern President Rejects Far Right Af D Involvement
May 01, 2025 -
 Klingbeil Zum Neuen Spd Fraktionsvorsitzenden Gewaehlt
May 01, 2025
Klingbeil Zum Neuen Spd Fraktionsvorsitzenden Gewaehlt
May 01, 2025
