Federal Investigation: Millions Stolen Through Office365 Breaches
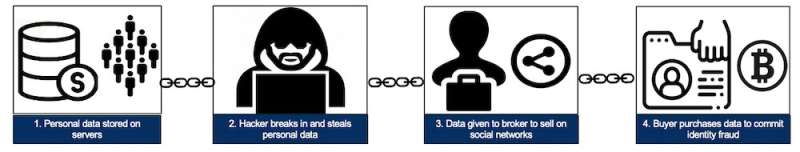
Table of Contents
Common Office365 Breach Tactics Used in Federal Investigations
Sophisticated attackers employ various tactics to compromise Office365 accounts, often leading to substantial financial losses and triggering federal investigations. Understanding these methods is the first step towards effective protection.
Phishing and Social Engineering
Phishing scams remain a primary vector for Office365 breaches. Attackers craft convincing emails mimicking legitimate organizations to trick users into revealing their credentials. These emails often exploit psychological vulnerabilities and leverage social engineering principles to increase their success rate.
- Examples: Emails appearing to be from internal IT, requesting password resets, or containing urgent requests for sensitive information. Spoofed emails from known vendors or delivery services are also common.
- Psychology: Attackers utilize urgency, fear, and authority to manipulate recipients into acting quickly without verifying the email's authenticity.
- Social Engineering: Attackers may engage in pretexting—pretending to be someone they are not—to gain access to information or manipulate employees into performing actions that compromise security.
Malware and Ransomware Attacks
Malicious software, including ransomware and other malware, is frequently used to gain unauthorized access to Office365 accounts. This can result in data theft, system disruption, and significant financial losses, often attracting the attention of federal investigators.
- Types of Malware: Viruses, Trojans, spyware, and ransomware are commonly used to infect systems and steal credentials or encrypt data.
- Methods of Infiltration: Infected email attachments, malicious links in phishing emails, and compromised websites are common entry points for malware.
- Consequences of Infection: Data breaches, financial losses, system downtime, and reputational damage can all stem from malware infections.
Exploiting Weak Passwords and Security Gaps
Weak passwords and inadequate security practices are significant vulnerabilities that attackers readily exploit. Many organizations fail to enforce strong password policies or implement multi-factor authentication (MFA), leaving their Office365 accounts vulnerable.
- Best Practices for Password Management: Enforce strong, unique passwords for each account; use a password manager to securely store and manage credentials.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring users to provide a second form of authentication (e.g., a code from their phone) in addition to their password.
- Regular Security Audits: Regularly review security policies and procedures to identify and address weaknesses.
The Scope and Impact of Office365 Data Breaches Leading to Federal Investigations
The consequences of Office365 data breaches extend far beyond immediate financial losses. They trigger legal and regulatory ramifications, severely impacting reputation and customer trust.
Financial Losses
Data breaches lead to significant financial losses, including direct costs associated with data recovery, legal fees, regulatory fines, and the cost of remediation. The financial impact can be crippling for many organizations.
- Examples: High-profile cases of data breaches have resulted in millions, even billions, of dollars in losses.
- Cost of Recovery and Remediation: The process of recovering data, restoring systems, and notifying affected individuals can be extremely costly.
- Potential Fines: Regulatory bodies can impose substantial fines for non-compliance with data protection regulations.
Legal and Regulatory Ramifications
Failing to protect sensitive data can lead to serious legal consequences, including federal investigations and hefty penalties. Regulations like GDPR and CCPA mandate strict data protection measures.
- Relevant Laws and Regulations: Organizations must comply with various data protection laws, depending on their location and the type of data they handle. Non-compliance can result in significant fines and legal action.
- Potential Lawsuits: Data breach victims may file lawsuits against organizations for negligence and failure to protect their data.
- Reputational Harm: The negative publicity surrounding a data breach can severely damage an organization's reputation.
Damage to Reputation and Customer Trust
A data breach erodes customer trust and can result in a long-term loss of business. Customers are increasingly wary of organizations that fail to protect their data.
- Loss of Customers: Customers may switch to competitors after a data breach.
- Difficulty Attracting New Clients: A damaged reputation can make it harder to attract new customers.
- Decreased Investor Confidence: Investors may lose confidence in organizations with a history of data breaches.
Protecting Your Organization from Office365 Breaches and Federal Investigation
Proactive security measures are essential to prevent Office365 breaches and avoid costly federal investigations.
Implementing Robust Security Measures
Strengthening your Office365 security requires a multi-faceted approach.
- MFA: Mandatory multi-factor authentication significantly reduces the risk of unauthorized access.
- Strong Password Policies: Implement and enforce strong password policies, including password complexity requirements and regular password changes.
- Regular Security Training for Employees: Educate employees about phishing scams, malware, and other security threats.
- Advanced Threat Protection: Utilize Microsoft's advanced threat protection features to detect and block malicious emails and attachments.
- Software Updates: Keep all software updated with the latest security patches.
Regular Security Audits and Vulnerability Assessments
Proactive security measures are crucial in identifying and mitigating vulnerabilities before they can be exploited.
- Penetration Testing: Simulate real-world attacks to identify weaknesses in your security systems.
- Security Audits: Regularly review your security policies and procedures to ensure they are effective.
- Vulnerability Assessments: Scan your systems for known vulnerabilities and address them promptly.
Incident Response Planning
Having a well-defined incident response plan is critical for minimizing the impact of a breach.
- Data Recovery: Establish procedures for data recovery in the event of a breach.
- Notification Procedures: Develop a plan for notifying affected individuals and regulatory bodies.
- Communication Strategies: Prepare communication materials to address the breach and reassure stakeholders.
Conclusion: Mitigating the Risk of Federal Investigation: Millions Stolen Through Office365 Breaches
Office365 breaches pose significant risks, leading to substantial financial losses, legal repercussions, and reputational damage. Implementing robust security measures, including MFA, strong password policies, regular security training, and proactive vulnerability assessments, is crucial for protecting your organization. Negligence can result in costly and damaging federal investigations. Don't become a statistic. Strengthen your Office365 security today by implementing the best practices outlined in this article and avoid costly and damaging federal investigations. Proactive security is not an expense; it's an investment in the future of your organization.

Featured Posts
-
 Waiting For A Call A Story Of Patience And Hope Or Despair
May 24, 2025
Waiting For A Call A Story Of Patience And Hope Or Despair
May 24, 2025 -
 M56 Delays Cheshire Deeside Border Collision Causes Traffic Disruption
May 24, 2025
M56 Delays Cheshire Deeside Border Collision Causes Traffic Disruption
May 24, 2025 -
 M62 Resurfacing Westbound Closure Between Manchester And Warrington
May 24, 2025
M62 Resurfacing Westbound Closure Between Manchester And Warrington
May 24, 2025 -
 Gambling On Calamity The Los Angeles Wildfires And Societal Shifts
May 24, 2025
Gambling On Calamity The Los Angeles Wildfires And Societal Shifts
May 24, 2025 -
 Alnmw Alqwy Ldaks 30 Tfwq Ela Twqeat Alswq Wtjawz Dhrwt Mars
May 24, 2025
Alnmw Alqwy Ldaks 30 Tfwq Ela Twqeat Alswq Wtjawz Dhrwt Mars
May 24, 2025
Latest Posts
-
 A Couples Hilarious Fight Over Joe Jonas His Response
May 24, 2025
A Couples Hilarious Fight Over Joe Jonas His Response
May 24, 2025 -
 Joe Jonass Mature Handling Of A Couples Argument
May 24, 2025
Joe Jonass Mature Handling Of A Couples Argument
May 24, 2025 -
 The Jonas Brothers Joe Jonas His Classy Response To A Fan Fight
May 24, 2025
The Jonas Brothers Joe Jonas His Classy Response To A Fan Fight
May 24, 2025 -
 Analyzing Jonathan Groffs Chances At A Tony Award For Just In Time
May 24, 2025
Analyzing Jonathan Groffs Chances At A Tony Award For Just In Time
May 24, 2025 -
 Joe Jonas His Response To A Couples Public Argument
May 24, 2025
Joe Jonas His Response To A Couples Public Argument
May 24, 2025
