Millions Made From Exec Office365 Account Hacks: Federal Investigation
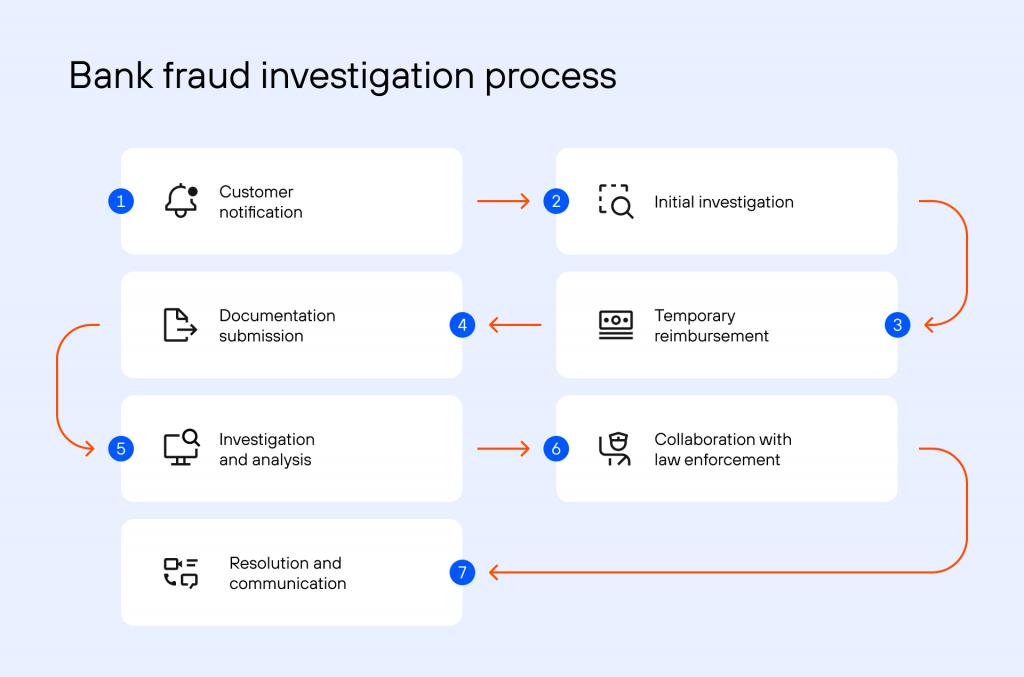
Table of Contents
The Methods Behind the Office365 Executive Account Hacks
Cybercriminals employ sophisticated techniques to compromise Office365 executive accounts, focusing on methods that bypass traditional security measures. These attacks often leverage social engineering and exploit weaknesses in user behavior and system vulnerabilities.
-
Phishing: Attackers send deceptive emails mimicking legitimate communications from trusted sources. These emails often contain malicious links or attachments designed to install malware or steal credentials. A well-crafted phishing email can trick even experienced users into revealing sensitive information.
-
Spear Phishing: This highly targeted approach involves researching specific individuals to personalize the phishing attack. Attackers gather information about their target, creating highly convincing emails that are more likely to succeed. Spear phishing emails often exploit current events or internal company information to increase their credibility.
-
Credential Stuffing: This brute-force attack uses lists of stolen usernames and passwords from other data breaches to try and gain access to Office365 accounts. Reusing passwords across multiple platforms significantly increases the risk of a successful credential stuffing attack.
-
Exploiting Third-Party App Vulnerabilities: Many businesses integrate third-party applications with their Office365 environment. If these apps have security vulnerabilities, attackers can exploit them to gain unauthorized access to accounts and data. Failing to regularly update and patch these apps leaves organizations vulnerable.
Real-world examples, like the recent attack on [mention a relevant example if available, citing a reputable source], demonstrate the effectiveness of these methods, highlighting the need for robust security protocols.
The Financial Impact of the Office365 Executive Account Breaches
The financial consequences of these Office365 executive account breaches are substantial, reaching into the millions of dollars for affected businesses. The cost extends beyond the immediate financial losses.
-
Direct Financial Losses: These include direct financial losses from fraudulent transactions, data theft, and ransomware demands. Attackers may use compromised accounts to transfer funds, steal intellectual property, or disrupt operations.
-
Indirect Costs: The indirect costs are equally significant and can include legal fees associated with investigations and lawsuits, the expense of damage control and reputational repair, and the loss of business due to operational disruptions and damaged trust.
The overall cost can be crippling for many businesses, impacting their bottom line and long-term viability. Experts estimate the cost of a data breach, including remediation and long-term impact, can easily reach millions, often significantly impacting a company's stock price and investor confidence.
The Federal Investigation and its Implications
A comprehensive federal investigation is underway, focusing on the widespread Office365 executive account hacks. Agencies such as the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) are actively involved.
-
Investigative Agencies: Multiple federal agencies are collaborating to identify and prosecute those responsible for these cybercrimes. Their efforts include tracing financial transactions, identifying the perpetrators, and building cases for prosecution.
-
Scope of the Investigation: The investigation is far-reaching, encompassing a wide range of victims and potential perpetrators. The investigation aims to disrupt criminal networks and prevent future attacks.
-
Legal and Regulatory Consequences: The consequences for those found guilty of these crimes can be severe, including significant fines, imprisonment, and reputational damage. The investigation also highlights the importance of complying with data protection regulations. This situation underscores the importance of proactive security measures.
Protecting Your Office365 Executive Accounts: Best Practices
Preventing Office365 executive account hacks requires a multi-layered approach encompassing technical security measures, employee training, and robust security policies.
-
Strong Passwords and Multi-Factor Authentication (MFA): Employ strong, unique passwords for all accounts and implement MFA to add an extra layer of security.
-
Security Awareness Training: Regular security awareness training for employees is crucial to educate them about phishing scams, spear phishing attacks, and other social engineering techniques.
-
Robust Security Measures: Implement robust security measures like intrusion detection and prevention systems (IDPS) to monitor network activity and identify potential threats.
-
Regular Software Updates and Patching: Regularly update software and patch vulnerabilities to prevent attackers from exploiting known weaknesses.
-
Data Encryption and Backup Strategies: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access, and maintain regular data backups to ensure business continuity in the event of a breach.
By adopting these best practices, businesses can significantly strengthen their Office365 security posture and reduce their risk of becoming victims of similar attacks.
Conclusion
The ongoing federal investigation into the millions lost from Office365 executive account hacks highlights the severity of this growing cybersecurity threat. The financial impact on businesses is devastating, extending far beyond direct financial losses to include reputational damage and long-term operational disruptions. To avoid becoming a victim, businesses must prioritize proactive security measures. Strengthen your Office365 security by implementing strong passwords, multi-factor authentication, and regular security awareness training. Protect your Office365 executive accounts by regularly patching vulnerabilities and investing in robust security solutions. Prevent Office365 breaches by adopting a comprehensive security strategy that addresses both technical and human vulnerabilities. Don't wait until it's too late – take action today to safeguard your organization's valuable data and reputation.

Featured Posts
-
 Dodgers Conforto Will He Duplicate Hernandezs Success
May 18, 2025
Dodgers Conforto Will He Duplicate Hernandezs Success
May 18, 2025 -
 Cybercriminal Nets Millions From Executive Office365 Account Breaches
May 18, 2025
Cybercriminal Nets Millions From Executive Office365 Account Breaches
May 18, 2025 -
 Thousands Experience Reddit Downtime Worldwide
May 18, 2025
Thousands Experience Reddit Downtime Worldwide
May 18, 2025 -
 Trump On Taylor Swift A Deep Dive Into The Maga Response
May 18, 2025
Trump On Taylor Swift A Deep Dive Into The Maga Response
May 18, 2025 -
 Dry Spell Could Dampen Easter Bonfire Celebrations
May 18, 2025
Dry Spell Could Dampen Easter Bonfire Celebrations
May 18, 2025
Latest Posts
-
 Amanda Bynes Only Fans Debut A New Chapter After Quitting Acting
May 18, 2025
Amanda Bynes Only Fans Debut A New Chapter After Quitting Acting
May 18, 2025 -
 Former Child Star Amanda Bynes Returns To The Public Eye With Only Fans
May 18, 2025
Former Child Star Amanda Bynes Returns To The Public Eye With Only Fans
May 18, 2025 -
 Amanda Bynes School Days A Classmates Perspective
May 18, 2025
Amanda Bynes School Days A Classmates Perspective
May 18, 2025 -
 Amanda Bynes A Classmates Account Of Past Events
May 18, 2025
Amanda Bynes A Classmates Account Of Past Events
May 18, 2025 -
 Drake Bells Comments On Amanda Bynes And The Rachel Green Reference
May 18, 2025
Drake Bells Comments On Amanda Bynes And The Rachel Green Reference
May 18, 2025
