Millions Stolen: Inside The Office365 Hack Targeting Executive Inboxes

Table of Contents
The Tactics Employed in the Office365 Executive Inbox Hack
The methods used in these Office365 executive inbox hacks are often surprisingly simple yet incredibly effective, leveraging social engineering and exploiting human weaknesses to gain access to sensitive information.
Spear Phishing and Impersonation
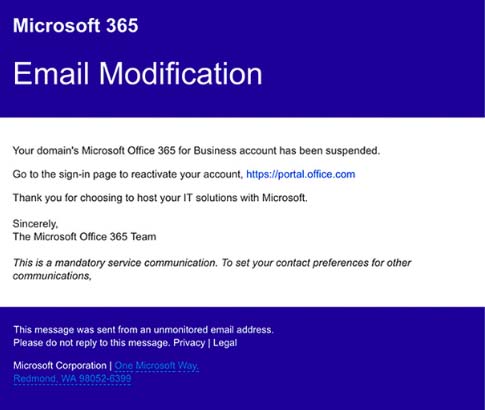
Spear phishing is a hallmark of these attacks. Attackers meticulously craft personalized emails that appear to come from trusted sources, such as a colleague, a client, or even the CEO. They leverage publicly available information to create highly convincing messages designed to bypass spam filters.
- Examples of convincing phishing emails: Emails requesting urgent wire transfers, sharing sensitive documents via seemingly legitimate links, or posing as an IT support representative needing access credentials.
- CEO fraud: Attackers impersonate the CEO or other high-level executives to instruct employees to make fraudulent payments.
- Exploiting known relationships: Attackers often research their targets, identifying connections and leveraging these relationships to create a more believable persona.
These sophisticated emails are designed to bypass spam filters by avoiding common red flags. The personalization is key; generic phishing emails are easily detected, but targeted spear phishing campaigns often slip through undetected.
Exploiting Weak Passwords and Multi-Factor Authentication Bypass
Even with robust security measures in place, weak passwords remain a major vulnerability. Attackers often employ brute-force attacks, password spraying, or even social engineering to obtain credentials. The lack of, or bypass of, multi-factor authentication (MFA) further exacerbates the risk.
- Common password mistakes: Using easily guessable passwords, reusing passwords across multiple accounts, and failing to change passwords regularly.
- Methods of MFA bypass: SIM swapping (redirecting phone calls and texts to the attacker's device to bypass SMS-based MFA), social engineering (tricking the user into revealing their MFA codes), or exploiting vulnerabilities in MFA systems.
- Password reuse: A single compromised password can provide access to numerous accounts, expanding the impact of the breach.
Strong, unique passwords and the mandatory implementation of robust multi-factor authentication are absolutely crucial for preventing access to executive inboxes.
Leveraging Compromised Credentials
Once initial access is gained, attackers often leverage compromised credentials to move laterally within the network, escalating their privileges to access more sensitive data and systems.
- Lateral movement techniques: Attackers use various techniques to move from one compromised account to another, gaining access to more sensitive data and systems.
- Exploitation of privilege escalation vulnerabilities: Attackers often exploit vulnerabilities within the network to gain higher-level access, allowing them to perform more damaging actions.
This expansion of access can lead to a significant data breach, extending far beyond the initially compromised executive inbox.
The Impact of the Office365 Executive Inbox Breach
The consequences of a successful Office365 executive inbox breach extend far beyond the immediate financial losses. The impact reverberates across the organization and can have long-term consequences.
Financial Losses
The financial ramifications of these attacks can be catastrophic. Attackers often use compromised accounts to initiate fraudulent wire transfers, demanding ransom payments, or stealing sensitive financial data.
- Examples of financial losses: Millions of dollars lost through fraudulent wire transfers to offshore accounts, extortion attempts targeting sensitive company information, and the costs associated with investigations and remediation.
The financial impact can cripple even the largest companies.
Reputational Damage
A data breach, particularly one involving the compromise of executive inboxes, severely damages an organization's reputation. This loss of trust can have lasting repercussions.
- Loss of customer trust: Customers may lose confidence in the company's ability to protect sensitive information, leading to a loss of business.
- Negative media coverage: Public disclosure of the breach can lead to negative media attention, further damaging the company's reputation.
- Impact on stock prices: The news of a data breach can negatively impact a company's stock price, resulting in significant financial losses.
The reputational damage can be as, or even more, devastating than the direct financial loss.
Legal and Regulatory Consequences
Businesses facing a data breach involving sensitive personal information face significant legal and regulatory consequences.
- GDPR fines: Non-compliance with the General Data Protection Regulation (GDPR) can result in hefty fines.
- Lawsuits: Companies may face lawsuits from affected individuals or customers.
- Regulatory investigations: Regulatory bodies may launch investigations, leading to further penalties and reputational damage.
The potential legal and regulatory repercussions underscore the critical need for robust cybersecurity measures.
Protecting Your Executive Inbox from Similar Attacks
Proactive measures are critical to prevent becoming a victim of these devastating attacks. A multi-layered approach is essential.
Implementing Robust Security Measures
Implementing a strong security posture requires a comprehensive approach.
- Multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain a password.
- Strong password policies: Enforce strong, unique passwords and regularly update password policies.
- Regular security awareness training: Educate employees about phishing techniques and social engineering tactics to improve their ability to recognize and report suspicious activity.
- Email filtering and spam protection: Implement robust email filtering and spam protection systems to prevent malicious emails from reaching inboxes.
- Endpoint detection and response (EDR): EDR solutions provide advanced threat detection and response capabilities to identify and mitigate threats on endpoints.
- Advanced threat protection (ATP): ATP solutions offer advanced protection against sophisticated threats like spear phishing and malware.
These measures significantly reduce the likelihood of a successful attack.
Investing in Cybersecurity Expertise
Don't underestimate the value of professional help.
- Regular security audits: Regular security audits identify vulnerabilities and weaknesses in your systems.
- Penetration testing: Penetration testing simulates real-world attacks to identify vulnerabilities before attackers can exploit them.
- Incident response planning: A well-defined incident response plan ensures a swift and effective response in case of a breach.
Professional cybersecurity expertise is invaluable.
Monitoring and Alerting Systems
Real-time monitoring is critical for early threat detection.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a comprehensive view of security events.
- User and Entity Behavior Analytics (UEBA): UEBA solutions detect anomalous user and entity behavior, indicating potential malicious activity.
These systems enable swift response to threats before they can cause significant damage.
Conclusion
The Office365 executive inbox hack is a serious threat with devastating consequences. The tactics used are sophisticated, and the impact can be financially and reputationally crippling. However, by implementing robust security measures, investing in cybersecurity expertise, and employing comprehensive monitoring and alerting systems, organizations can significantly reduce their risk. Don't wait until it's too late. Proactively enhance your Office365 security today and prevent becoming the next victim of an executive inbox compromise. For further information on bolstering your cybersecurity defenses, explore resources from reputable cybersecurity organizations and consult with security professionals to tailor a solution specific to your needs. Protecting your executive inbox is not just a best practice – it's a necessity in today's threat landscape.

Featured Posts
-
 Our Yorkshire Farm Amanda Owen Breaks Down In Emotional Farewell
Apr 30, 2025
Our Yorkshire Farm Amanda Owen Breaks Down In Emotional Farewell
Apr 30, 2025 -
 4 Kwietnia Miedzynarodowy Dzien Zwierzat Bezdomnych Jak Mozesz Pomoc
Apr 30, 2025
4 Kwietnia Miedzynarodowy Dzien Zwierzat Bezdomnych Jak Mozesz Pomoc
Apr 30, 2025 -
 Trumps Election Claims Days Before Canadian Vote Us Canada Relations Tense
Apr 30, 2025
Trumps Election Claims Days Before Canadian Vote Us Canada Relations Tense
Apr 30, 2025 -
 High Profile Office365 Hack Results In Millions In Losses For Executives
Apr 30, 2025
High Profile Office365 Hack Results In Millions In Losses For Executives
Apr 30, 2025 -
 Lempron Tzeims I Epoxi Ton 50 000 Ponton
Apr 30, 2025
Lempron Tzeims I Epoxi Ton 50 000 Ponton
Apr 30, 2025
Latest Posts
-
 Il Caso Becciu Preghiere Dimissioni E Prospettive Future
Apr 30, 2025
Il Caso Becciu Preghiere Dimissioni E Prospettive Future
Apr 30, 2025 -
 Mario Nanni Omaggio A Un Grande Giornalista Parlamentare
Apr 30, 2025
Mario Nanni Omaggio A Un Grande Giornalista Parlamentare
Apr 30, 2025 -
 Chat E Complotto Le Rivelazioni Di Domani Sul Caso Becciu
Apr 30, 2025
Chat E Complotto Le Rivelazioni Di Domani Sul Caso Becciu
Apr 30, 2025 -
 L Impatto Delle Preghiere Sulla Decisione Di Becciu Riguardo Alle Dimissioni
Apr 30, 2025
L Impatto Delle Preghiere Sulla Decisione Di Becciu Riguardo Alle Dimissioni
Apr 30, 2025 -
 Lutto Nel Giornalismo Parlamentare Ci Lascia Mario Nanni
Apr 30, 2025
Lutto Nel Giornalismo Parlamentare Ci Lascia Mario Nanni
Apr 30, 2025
