Office365 Data Breach: Millions Stolen, Crook Charged
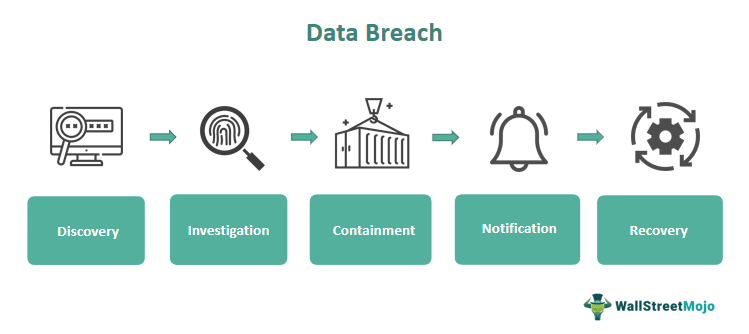
Table of Contents
The Scale of the Office365 Data Breach and its Impact
The Office365 data breach exposed the sensitive information of countless individuals and organizations. While the exact number of compromised accounts remains under investigation, reports suggest millions were affected. The types of data stolen included emails, customer lists, financial records, and intellectual property, representing a significant blow to affected businesses. The impact extends far beyond the immediate loss of data:
-
Financial Loss: The cost of recovering from a data breach is substantial. Affected businesses face expenses related to investigation, remediation, legal fees, notification of affected individuals, and credit monitoring services. Estimates suggest losses can reach millions of dollars, depending on the scale of the breach and the nature of the stolen data.
-
Reputational Damage: A data breach severely erodes customer trust. The loss of sensitive information can lead to a decline in customer loyalty and damage to brand reputation, impacting future business opportunities. The negative publicity surrounding a breach can be long-lasting.
-
Legal Consequences: Businesses face significant legal repercussions following a data breach. Depending on the jurisdiction and the nature of the data compromised, companies may face hefty fines and lawsuits from affected individuals and regulatory bodies for non-compliance with data protection laws like GDPR.
-
Examples of Sensitive Data Compromised: The breach included highly sensitive data such as personally identifiable information (PII), bank account details, trade secrets, and confidential client communications.
How the Office365 Data Breach Occurred – Identifying Vulnerabilities
The investigation revealed that the criminal employed a combination of techniques to gain unauthorized access to Office365 accounts. While the precise methods used are still emerging, the breach highlights several common vulnerabilities:
-
Phishing Attacks: The perpetrator likely used sophisticated phishing emails designed to trick employees into revealing their login credentials. These emails often mimic legitimate communications from trusted sources.
-
Weak Passwords: Many organizations lack robust password policies, making it easier for attackers to guess or crack passwords through brute-force attacks or credential stuffing (using stolen credentials from other breaches).
-
Lack of Multi-Factor Authentication (MFA): The absence of MFA significantly weakens security. Even if an attacker obtains a username and password, MFA adds an extra layer of protection, requiring a second verification method (e.g., a code sent to a mobile phone).
-
Weaknesses in Security Protocols: The affected organizations might have overlooked essential security protocols or failed to implement appropriate security updates, leaving their systems vulnerable to exploitation.
The Arrest and Legal Proceedings – A Case Study in Cybercrime
Law enforcement agencies successfully tracked down and arrested the individual responsible for the Office365 data breach. Charges include unauthorized access to computer systems, data theft, and potentially other related offenses. The legal proceedings highlight the increasing focus on prosecuting cybercriminals and the seriousness of data breaches.
-
Details of the Arrest and Charges: The arrest demonstrates the commitment of law enforcement to combating cybercrime and pursuing those responsible for data breaches. The charges filed reflect the severity of the offenses.
-
The Role of Law Enforcement and Cybersecurity Agencies: This case showcases the crucial collaborative effort between law enforcement and cybersecurity agencies in investigating and prosecuting cybercrimes.
-
Potential Sentencing and Legal Ramifications: The perpetrator faces significant prison time and substantial fines. This case serves as a deterrent to other potential cybercriminals.
Strengthening Office365 Security – Best Practices and Prevention
Preventing future Office365 data breaches requires a proactive approach to security. Businesses must adopt and implement best practices:
-
Implementing Multi-Factor Authentication (MFA): MFA is non-negotiable. It significantly reduces the risk of unauthorized access, even if credentials are compromised.
-
Regular Security Audits and Penetration Testing: Regular assessments identify vulnerabilities and weaknesses in the system before attackers can exploit them.
-
Employee Security Awareness Training: Educating employees about phishing scams, password security, and other cybersecurity threats is critical. Regular training keeps employees vigilant against malicious activities.
-
Utilizing Advanced Threat Protection Features within Office365: Microsoft offers advanced threat protection features, such as anti-phishing and anti-malware capabilities, which should be fully utilized.
-
Regular Software Updates and Patching: Keeping software updated and patched is crucial to mitigating vulnerabilities exploited by attackers.
Conclusion
The Office365 data breach serves as a stark warning. The consequences of inadequate data security – financial losses, reputational damage, and legal penalties – are far-reaching and devastating. The successful prosecution of the perpetrator offers a measure of justice, but it is imperative that businesses take proactive steps to protect themselves. Review your Office365 security settings, implement the best practices outlined above, and consider investing in advanced security solutions. Don't wait for an Office365 data breach to strike – take control of your data security today. Investing in robust security measures is not just a cost; it's an investment in the future of your business.

Featured Posts
-
 Tragic Fate Of Americas First Non Binary Person
May 10, 2025
Tragic Fate Of Americas First Non Binary Person
May 10, 2025 -
 La Fires Real Estate Agent Exposes Landlord Price Gouging Practices
May 10, 2025
La Fires Real Estate Agent Exposes Landlord Price Gouging Practices
May 10, 2025 -
 Controversy Surrounding Ag Pam Bondi And The Epstein Client List
May 10, 2025
Controversy Surrounding Ag Pam Bondi And The Epstein Client List
May 10, 2025 -
 Elon Musk Jeff Bezos And Mark Zuckerberg Billions Lost Since January 20 2017
May 10, 2025
Elon Musk Jeff Bezos And Mark Zuckerberg Billions Lost Since January 20 2017
May 10, 2025 -
 Alterya Acquired By Chainalysis A Boost For Blockchain Security And Analytics
May 10, 2025
Alterya Acquired By Chainalysis A Boost For Blockchain Security And Analytics
May 10, 2025
Latest Posts
-
 Finding The Real Safe Bet Strategies For Risk Averse Investors
May 10, 2025
Finding The Real Safe Bet Strategies For Risk Averse Investors
May 10, 2025 -
 The Real Safe Bet A Practical Guide To Secure Investments
May 10, 2025
The Real Safe Bet A Practical Guide To Secure Investments
May 10, 2025 -
 Stock Market Update Sensex Nifty 50 Unchanged Amidst Geopolitical Concerns
May 10, 2025
Stock Market Update Sensex Nifty 50 Unchanged Amidst Geopolitical Concerns
May 10, 2025 -
 Povernennya Kinga Politichni Poglyadi Ta Kritika
May 10, 2025
Povernennya Kinga Politichni Poglyadi Ta Kritika
May 10, 2025 -
 India Stock Market Today Sensex And Nifty 50 Close Choppy Trading Session
May 10, 2025
India Stock Market Today Sensex And Nifty 50 Close Choppy Trading Session
May 10, 2025
