Transferred Data: A Comprehensive Guide To Secure Data Migration
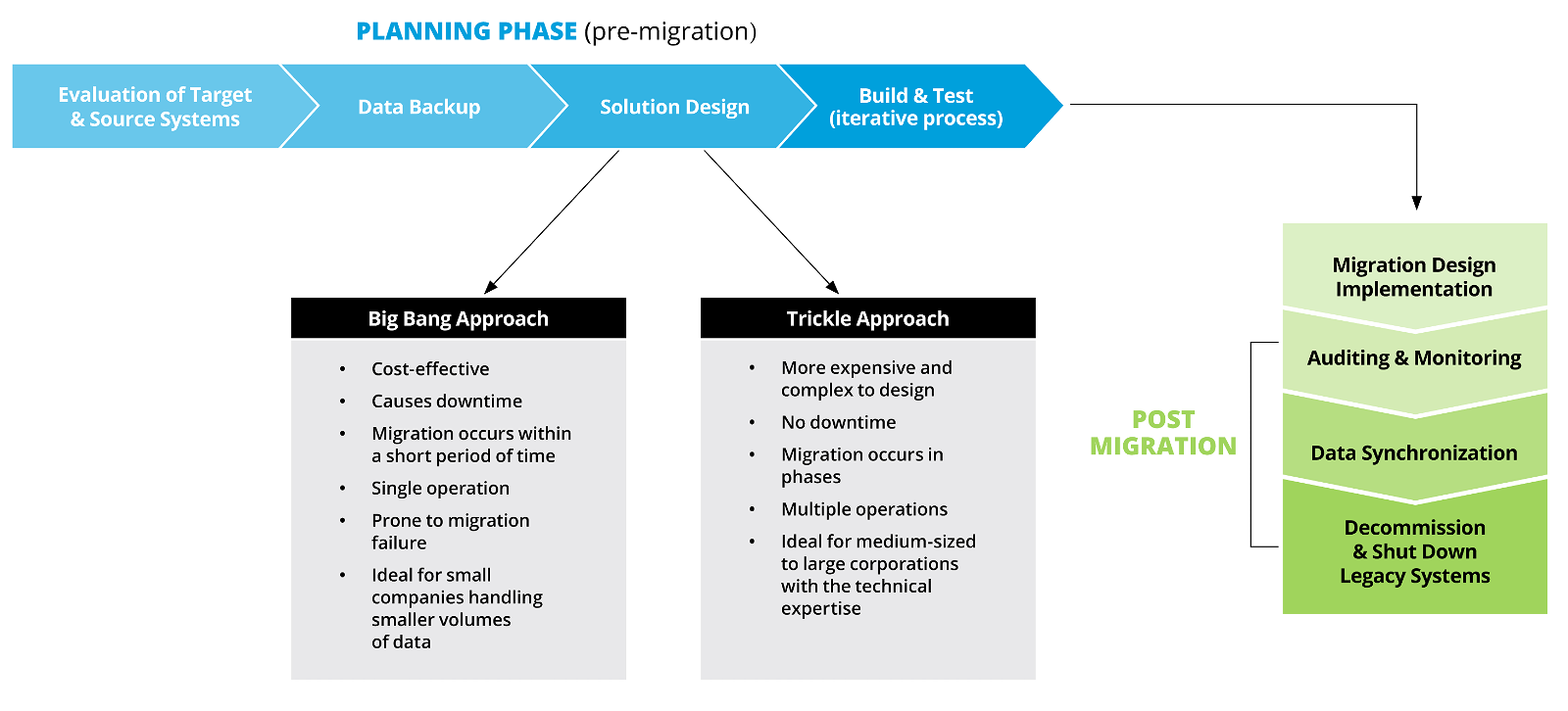
Table of Contents
Planning Your Data Migration Strategy
Before initiating any data transfer, a robust plan is paramount. This involves a thorough assessment of your current data landscape, careful selection of the migration method, and a precise definition of your security requirements.
Assessing Your Current Data Landscape
Understanding your existing data environment is the foundation of a successful data migration. This involves a detailed data assessment, including:
- Data Inventory: Create a comprehensive list of all your data systems, databases, and files. Identify the location, size, and type of each data source.
- Data Categorization: Classify your data based on sensitivity levels (e.g., confidential, sensitive, public). This helps determine the appropriate security controls needed during the transfer.
- Data Dependency Mapping: Analyze the relationships between different data sets to avoid breaking dependencies during the migration. Understand how data flows between systems.
- Data Analysis: Evaluate data quality and identify any inconsistencies or duplicates that need to be addressed before migration.
Effective data analysis is critical for efficient data mapping and helps prevent data loss during the migration process. This step is often overlooked but is crucial for minimizing risks.
Choosing the Right Migration Method
The method you choose for your data migration significantly impacts the security and efficiency of the process. Common approaches include:
- Cloud Migration: Moving data to a cloud-based infrastructure offers scalability and cost-effectiveness. Strategies include:
- Lift and Shift: A straightforward approach where applications and data are moved to the cloud with minimal changes.
- Replatforming: Migrating applications to a different cloud platform, often involving some modifications.
- Refactoring: Significant changes to applications to optimize them for the cloud environment.
- On-Premise Migration: Transferring data within your existing on-premise infrastructure. This is often simpler but might lack the scalability of cloud solutions.
- Hybrid Migration: A combination of cloud and on-premise solutions, balancing benefits and mitigating risks.
The optimal choice depends on factors like budget, technical expertise, and the specific needs of your organization. Carefully weigh the pros and cons of each method to ensure alignment with your overall data transfer goals. Consider using specialized migration tools to streamline the process.
Defining Your Security Requirements
Security should be at the forefront of your data migration planning. Establish clear security requirements encompassing:
- Data Encryption: Implement robust encryption for data both in transit (while being transferred) and at rest (when stored).
- Access Control: Restrict access to sensitive data during the migration, ensuring only authorized personnel can view or modify it. Use role-based access control (RBAC) for granular permissions.
- Compliance: Adhere to relevant data protection regulations, such as GDPR, HIPAA, CCPA, and others, depending on your industry and location.
Implementing Secure Data Transfer
With a solid plan in place, the next step is the secure implementation of your data transfer.
Selecting Secure Transfer Methods
Choosing the right data transfer method is critical for data security. Consider these options:
- Secure File Transfer Protocol (SFTP): A secure protocol for transferring files over a network, offering encryption and authentication.
- HTTPS: The secure version of HTTP, commonly used for transferring data over the internet, providing encryption and data integrity checks.
- VPNs (Virtual Private Networks): Create a secure, encrypted connection over a public network, enhancing security during data transmission.
- Dedicated Network Connections: Provide a private and secure connection for transferring large amounts of data, often used for high-security migrations.
The choice depends on the volume, sensitivity, and distance of the data transfer. Consider factors like bandwidth, latency, and security requirements.
Monitoring and Logging Data Transfers
Real-time monitoring and comprehensive logging are essential for maintaining data security and ensuring accountability.
- Real-time Monitoring: Track data transfer progress, identifying any anomalies or potential security breaches.
- Logging Mechanisms: Record detailed logs of all data transfer activities, including timestamps, users, and data volumes.
- Intrusion Detection Systems (IDS): Implement IDS to detect and alert you to any unauthorized access or malicious activity during the transfer.
These measures facilitate timely responses to security incidents and assist in post-migration audits.
Ensuring Data Integrity During Transfer
Maintaining data integrity throughout the transfer is crucial to prevent data loss or corruption.
- Checksums/Hash Functions: Generate checksums or hash values before and after the transfer to verify data accuracy. Any discrepancies indicate potential corruption.
- Data Validation Techniques: Implement validation rules to ensure data consistency and completeness.
- Automated Data Comparison Tools: Utilize tools to automatically compare data before and after transfer, highlighting any differences.
These methods ensure the transferred data matches the original data, maintaining its reliability and integrity.
Post-Migration Security and Maintenance
Even after the data migration is complete, ongoing security measures are vital to protect your transferred data.
Verifying Data Integrity and Accuracy
Post-migration verification is crucial to ensure the successful and accurate transfer of data.
- Data Validation Procedures: Perform thorough validation checks to confirm data accuracy and consistency in the new system.
- Testing: Test the functionality of the new system to identify any issues related to data integrity or accessibility.
- Accessibility: Ensure all migrated data is readily and securely accessible to authorized users.
This step is critical in confirming a successful migration and identifying any potential problems early on.
Ongoing Security Monitoring and Updates
Maintaining security is an ongoing process. Implement these continuous security measures:
- Regular Security Audits: Conduct periodic audits to assess the security posture of your systems and identify vulnerabilities.
- System Updates and Patching: Keep your systems updated with the latest security patches to protect against known vulnerabilities.
- Employee Training: Provide regular training to employees on security best practices and data protection policies.
Continuous monitoring and updates are key to mitigating emerging threats and maintaining a secure environment for your transferred data.
Conclusion
Securing your transferred data requires a comprehensive approach encompassing careful planning, secure implementation, and ongoing maintenance. By following the steps outlined in this guide – from conducting a thorough data assessment and choosing the right migration method to implementing robust security protocols and performing post-migration verification – you can significantly reduce the risks associated with data transfer and ensure the safety and integrity of your valuable information. Don't risk data breaches; ensure the safety of your transferred data with a well-planned migration strategy. Contact us today for expert guidance on secure data migration and let us help you navigate this critical process.

Featured Posts
-
 Xrp Price Surge Outperforming Bitcoin Post Sec Grayscale Etf Filing Recognition
May 08, 2025
Xrp Price Surge Outperforming Bitcoin Post Sec Grayscale Etf Filing Recognition
May 08, 2025 -
 Solana Vs Xrp Etf Buzz Propels Xrp To Higher Trading Volumes
May 08, 2025
Solana Vs Xrp Etf Buzz Propels Xrp To Higher Trading Volumes
May 08, 2025 -
 Nikola Jokic To Sit Out Nuggets Give Starters Rest Post Double Ot Loss
May 08, 2025
Nikola Jokic To Sit Out Nuggets Give Starters Rest Post Double Ot Loss
May 08, 2025 -
 Will Grayscales Etf Filing Push Xrp To New Record Highs
May 08, 2025
Will Grayscales Etf Filing Push Xrp To New Record Highs
May 08, 2025 -
 Lyon Cede Ante El Psg En Casa
May 08, 2025
Lyon Cede Ante El Psg En Casa
May 08, 2025
Latest Posts
-
 Aprel 2025 V Permi I Permskom Krae Prognoz Pogody S Uchetom Pokholodaniya I Vozmozhnykh Snegopadov
May 09, 2025
Aprel 2025 V Permi I Permskom Krae Prognoz Pogody S Uchetom Pokholodaniya I Vozmozhnykh Snegopadov
May 09, 2025 -
 Imalaia Elaxista Xionia Epiptoseis Sto Oikosystima Kai Toys Plithysmoys
May 09, 2025
Imalaia Elaxista Xionia Epiptoseis Sto Oikosystima Kai Toys Plithysmoys
May 09, 2025 -
 Bayern Munich Vs Fc St Pauli Match Preview And Prediction
May 09, 2025
Bayern Munich Vs Fc St Pauli Match Preview And Prediction
May 09, 2025 -
 The Colin Cowherd Effect How Criticism Shapes The Perception Of Jayson Tatum
May 09, 2025
The Colin Cowherd Effect How Criticism Shapes The Perception Of Jayson Tatum
May 09, 2025 -
 Xionia Sta Imalaia Sto Xamilotero Simeio Ton Teleytaion 23 Eton
May 09, 2025
Xionia Sta Imalaia Sto Xamilotero Simeio Ton Teleytaion 23 Eton
May 09, 2025
