Office365 Data Breach Nets Hacker Millions, Federal Investigation Reveals

Table of Contents
The Scale and Scope of the Office365 Data Breach
The Office365 data breach exposed a significant amount of sensitive information, causing substantial financial and reputational damage. The extent of the compromise was far-reaching, impacting various aspects of the victim company's operations.
- Types of data stolen: The breach compromised customer data including Personally Identifiable Information (PII), financial records, intellectual property, and confidential business communications. This sensitive data is highly valuable to cybercriminals for identity theft, financial fraud, and competitive advantage.
- Number of affected users/records: While the exact number of affected users remains undisclosed for privacy reasons, the investigation suggests thousands of records were accessed and exfiltrated. This highlights the potential for widespread impact even with seemingly targeted attacks.
- Financial impact on the victimized company: The financial losses incurred by the company are estimated to be in the millions of dollars, encompassing direct losses from stolen funds, legal fees associated with data breach notification and regulatory compliance, and the long-term costs of remediation and recovery efforts. This demonstrates the significant financial burden associated with such a breach.
- Specific vulnerabilities exploited: The investigation revealed that the breach exploited several vulnerabilities, including the use of weak passwords, a lack of multi-factor authentication (MFA), and successful spear-phishing attacks targeting employees with high-level access. These weaknesses underscore the critical importance of a comprehensive security posture.
The Federal Investigation: Uncovering the Hacker's Methods
The federal investigation meticulously pieced together the hacker's methods, uncovering a sophisticated and well-planned attack. Law enforcement used various digital forensic techniques to trace the perpetrators' activities.
- Techniques used by hackers to gain access: The hackers employed a combination of spear-phishing emails containing malicious attachments and exploiting known vulnerabilities in older versions of Office365 software. This combined approach increased the likelihood of successful infiltration.
- The hacker's infrastructure and methods of exfiltration: Investigators traced the exfiltrated data to servers located overseas, highlighting the transnational nature of cybercrime and the challenges associated with international collaboration in such investigations. The data was exfiltrated using encrypted channels and anonymization techniques to hinder detection.
- The role of compromised credentials: The investigation confirmed that compromised employee credentials played a critical role in the breach, allowing the hackers to gain initial access to the network and move laterally to access sensitive data. This highlights the importance of strong password policies and employee training.
- Evidence gathered during the investigation: The investigation gathered substantial digital forensic evidence, including network logs, email headers, and data recovered from the compromised servers, providing a detailed picture of the attack timeline and the hackers' methods. This evidence is crucial for future prosecutions and for improving overall cybersecurity defenses.
Lessons Learned and Best Practices for Office365 Security
The Office365 data breach provides crucial lessons for organizations seeking to bolster their cybersecurity defenses. The investigation underscores the need for a multi-layered security approach.
- Importance of multi-factor authentication (MFA): MFA is a crucial layer of security that significantly reduces the risk of unauthorized access even if credentials are compromised. Implementing MFA across all Office365 accounts is paramount.
- Regular security audits and vulnerability assessments: Regularly assessing the security posture of your Office365 environment helps identify and remediate vulnerabilities before they can be exploited by attackers.
- Employee security awareness training (phishing awareness): Employees are often the weakest link in the security chain. Comprehensive training on phishing techniques and social engineering tactics can significantly reduce the risk of successful attacks.
- Strong password policies and password management tools: Enforcing strong password policies and utilizing password management tools can significantly reduce the risk of weak or compromised credentials.
- Regular software updates and patching: Keeping Office365 software and all related applications up-to-date with the latest security patches is crucial to mitigate known vulnerabilities.
- Data encryption and access control: Encrypting sensitive data both in transit and at rest helps protect it even if it is compromised. Implementing robust access control mechanisms limits who can access sensitive information.
- Incident response planning: Having a comprehensive incident response plan in place is essential for minimizing the impact of a data breach. This plan should detail procedures for detection, containment, eradication, recovery, and post-incident activities.
The High Cost of Inaction: Financial and Reputational Damage
Beyond the immediate financial losses, the consequences of an Office365 data breach can be far-reaching and long-lasting.
- Regulatory fines and legal fees: Non-compliance with data privacy regulations can lead to substantial fines and legal fees. Organizations must understand and comply with regulations such as GDPR and CCPA.
- Loss of customer trust and brand reputation: A data breach can severely damage an organization's reputation and erode customer trust, leading to lost business and reduced revenue.
- Impact on stock prices (if applicable): For publicly traded companies, a data breach can negatively impact stock prices, resulting in significant financial losses for shareholders.
- Long-term recovery costs: Recovering from a data breach involves significant costs, including forensic investigations, legal fees, notification costs, credit monitoring services for affected customers, and system remediation.
Conclusion
The Office365 data breach detailed in this federal investigation serves as a stark reminder of the ever-present threat of cyberattacks. The significant financial losses and reputational damage suffered highlight the critical need for proactive and comprehensive cybersecurity strategies. Don't become the next victim of an Office365 data breach. Implement robust security measures, including multi-factor authentication, regular security audits, and employee training, to protect your sensitive data and safeguard your organization from devastating consequences. Invest in your Office365 security today.

Featured Posts
-
 5 Circuits Velo Pour Decouvrir La Loire Nantes Et L Estuaire
May 22, 2025
5 Circuits Velo Pour Decouvrir La Loire Nantes Et L Estuaire
May 22, 2025 -
 Jail Sentence For Antiques Roadshow Pair National Treasure Smuggling
May 22, 2025
Jail Sentence For Antiques Roadshow Pair National Treasure Smuggling
May 22, 2025 -
 Cassis Blackcurrant Cultivation Harvesting And Its Unique Characteristics
May 22, 2025
Cassis Blackcurrant Cultivation Harvesting And Its Unique Characteristics
May 22, 2025 -
 Moncoutant Sur Sevre L Histoire De Clisson Et Un Siecle De Diversification
May 22, 2025
Moncoutant Sur Sevre L Histoire De Clisson Et Un Siecle De Diversification
May 22, 2025 -
 Posthaste Signs Of A Canadian Real Estate Market Correction
May 22, 2025
Posthaste Signs Of A Canadian Real Estate Market Correction
May 22, 2025
Latest Posts
-
 Core Weave Stock Crwv Reacts To Nvidias Strategic Investment
May 22, 2025
Core Weave Stock Crwv Reacts To Nvidias Strategic Investment
May 22, 2025 -
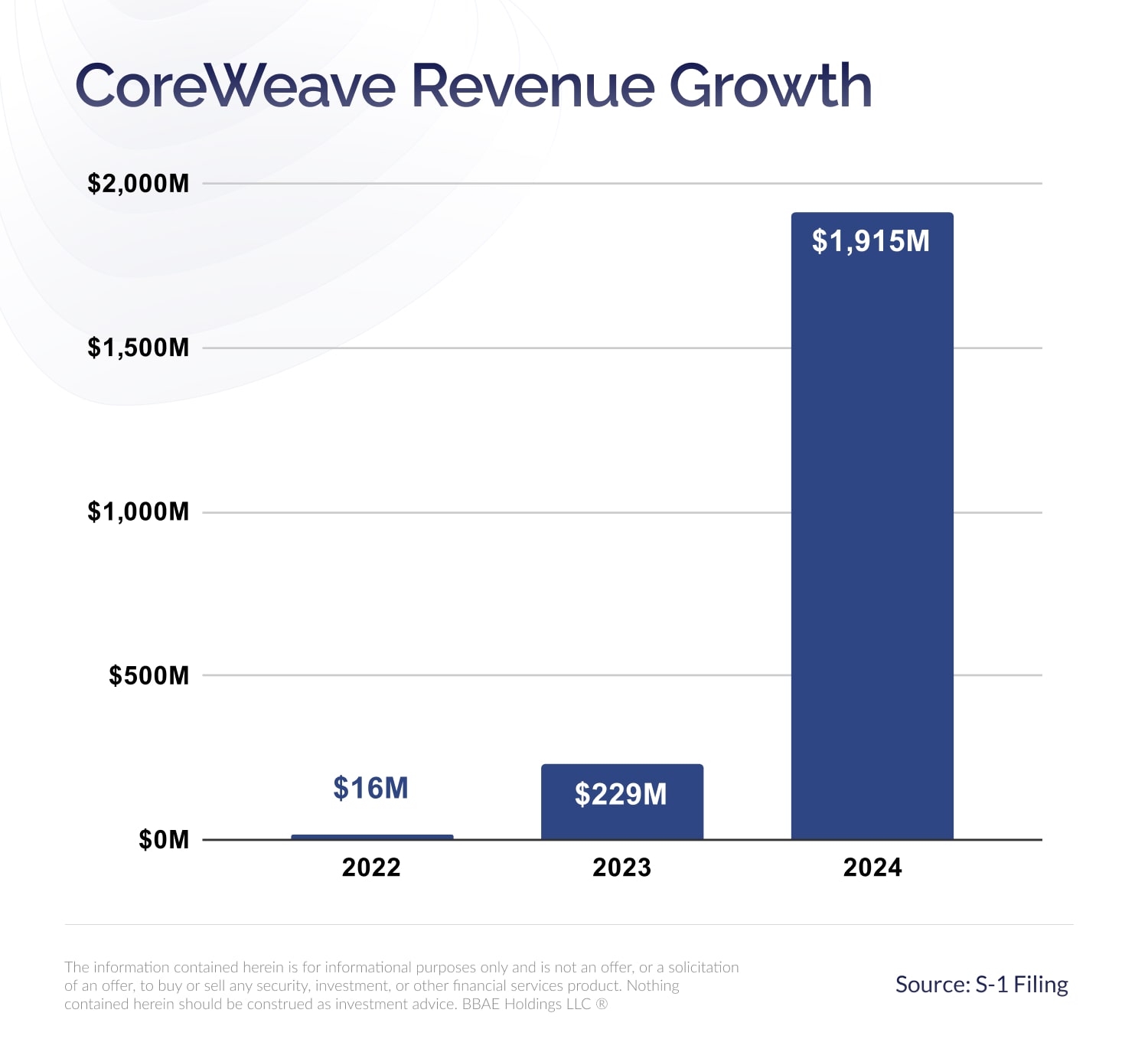 Core Weave Crwv Stock Market Performance Explaining Todays Gains
May 22, 2025
Core Weave Crwv Stock Market Performance Explaining Todays Gains
May 22, 2025 -
 Why Did Core Weave Crwv Stock Price Rise Today An Analysis
May 22, 2025
Why Did Core Weave Crwv Stock Price Rise Today An Analysis
May 22, 2025 -
 Core Weave Inc Crwv Stock Soars Reasons Behind The Increase
May 22, 2025
Core Weave Inc Crwv Stock Soars Reasons Behind The Increase
May 22, 2025 -
 Jim Cramers Investment Thesis Core Weave Crwv And The Ai Revolution
May 22, 2025
Jim Cramers Investment Thesis Core Weave Crwv And The Ai Revolution
May 22, 2025
